Friday, April 28, 2006
The Use by Banks of Non-SSL Login Forms
Fridays are for Fun - Judge creates own Da Vinci code
 Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.
Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.Seemingly random italicized letters were included in the 71-page judgment given by Mr Justice Peter Smith, which apparently spell out a message.
Mr Justice Smith said he would confirm the code if someone broke it.
"I can't discuss the judgment, but I don't see why a judgment should not be a matter of fun," he said.
You can check it out for yourself here.
Thursday, April 27, 2006
Security Myths and Passwords
Policies requiring regular password changes (e.g., monthly) are an example of exactly this form of infosec folk wisdom.
From a high-level perspective, let me observe that one problem with any widespread change policy is that it fails to take into account the various threats and other defenses that may be in place. Policies should always be based on a sound understanding of risks, vulnerabilities, and defenses. “Best practice” is intended as a default policy for those who don’t have the necessary data or training to do a reasonable risk assessment.
Tuesday, April 25, 2006
Tool Time - Cmos password recovery tools 4.8
Works with the following BIOSes
* ACER/IBM BIOS
* AMI BIOS
* AMI WinBIOS 2.5
* Award 4.5x/4.6x/6.0
* Compaq (1992)
* Compaq (New version)
* IBM (PS/2, Activa, Thinkpad)
* Packard Bell
* Phoenix 1.00.09.AC0 (1994), a486 1.03, 1.04, 1.10 A03, 4.05 rev 1.02.943, 4.06 rev 1.13.1107
* Phoenix 4 release 6 (User)
* Gateway Solo - Phoenix 4.0 release 6
* Toshiba
* Zenith AMI
With CmosPwd, you can also backup, restore and erase/kill cmos.
Cain & Abel v2.8.9 released
- Added hashes syncronization functions (Export/Import) to/from Cain for PocketPC via ActiveSync.
- Added VoIP sniffer support for the following codecs: G723.1, G726-16, G726-24, G726-32, G726-40, LPC-10.
- Added support for Winpcap v3.2.
Download here.
Monday, April 24, 2006
Home Security - Man dies when large hole opens in home
Full story here.It was like a scene from a horror film: A 27-year-old man plummeted into a gaping hole that suddenly opened beneath a house, trapping him beneath foundation rubble and killing him.
"It's unbelievable," Placer County Sheriff's Department spokeswoman Dena Erwin said. "From the front of the house, it's absolutely normal. Then, in the middle of the house, is this enormous hole."
The victim was awake and on the ground floor about 9:30 p.m. Friday when the concrete foundation near the kitchen gave way, sending him plunging into to the ground, Erwin said.
Saturday, April 22, 2006
Super-Glue: Best practice for countering key stroke loggers

Read all the details in this article.
The one thing not mention in the article is that it is reported that Sumitomo Bank's best practice for avoiding a repeat attack is that they now super-glue the keyboard connections into the backs of their PCs.
Tuesday, April 18, 2006
Image stealing by phishers
From F-Secure Blog...
Lazy phishers are often simply making a copy of the original bank site with some malicious modifications. As an example, take a look at this currently active phishing site targeting Chase Bank.
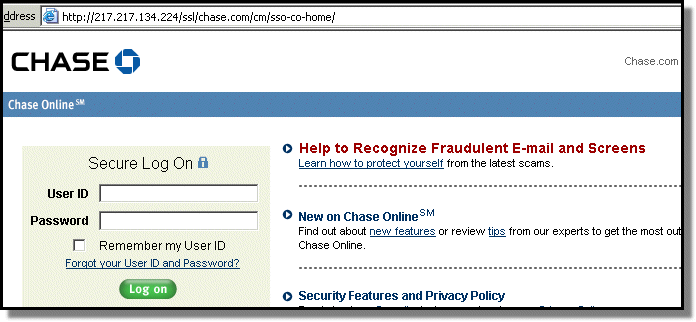
This phishing site is running on an infected home computer in Spain. Only the html is hosted there; all the images are actually loaded directly from a real chase.com server.
Now, activity like this could be detected by the website of the bank automatically. How about modifying the logic of the bank web server to do something along these lines:
If somebody
a) loads my images but
b) does not load the corresponding html file and
c) has http referrer -values outside of my domain
then, for this user, lets change this image:
to this image:

This could be activated only after the activity has happened from, say, 10 different IP addresses, to make it harder for the attackers to spot it until it's too late.
And, in most cases the REFERRER fields would directly point the bank staff to the real phishing site which they could now start closing down.
Eventually, attackers would move to host their own images, but for now they still typically don't.
Monday, April 17, 2006
Triple-DES Upgrade Adding Insecurities?
In a press release today, Redspin, an independent auditing firm based in Carpinteria, CA, suggests that the recent mandated upgrades of ATMs to support triple DES encryption of PINs has introduced new vulnerabilities into the ATM network environment - because of other changes that were typically made concurrently with the triple DES upgrades.
Sunday, April 16, 2006
Personal Security - So... You Think the Cold War is Over?
In a rare news conference, the designer of Russia's intercontinental ballistic missiles dismissed on Thursday a warning that Russia was falling behind the United States in the number of active nuclear warheads it has and said his Topol-M and Bulava missiles would serve as a sufficient deterrent until at least 2040.
"I assure you that the number of active warheads the strategic nuclear forces will have in 2015 and even in 2020 will be no less than 2,000," said Yury Solomonov, head and chief designer at the Moscow Institute of Thermal Technology, Russia's leading designer of intercontinental missiles.
Saturday, April 15, 2006
US Military Buys Back Stolen Flash Drives from Afghan Shopkeepers
Maps, charts, and intelligence reports on computer drives smuggled out of a US base and sold at a local bazaar describe how Taliban and Al Qaeda leaders have been using southwestern Pakistan as a key planning and training base for attacks in Afghanistan.
The documents, marked ''secret," appear to be raw intelligence reports based on conversations with Afghan informants, and official briefings given to high-level US military officers. Together, they outline how the US military came to focus its search for members of Taliban, Al Qaeda, and other terrorist groups on the border region with Pakistan and Pakistani territory.
American investigators have paid thousands of dollars to buy back the stolen drives, according to shopkeepers outside the major military base here, but many were still on sale yesterday.
Included on some drives were the Social Security numbers of hundreds of US soldiers, including four generals, and lists of troops who completed nuclear, chemical, and biological warfare training, the Associated Press reported.
Wednesday, April 12, 2006
Saturday, April 08, 2006
Forensic Analysis of the Windows Registry
Windows registry contains lots of information that are of potential evidential value or helpful in aiding forensic examiners on other aspects of forensic analysis. This paper discusses the basics of Windows XP registry and its structure, data hiding techniques in registry, and analysis on potential Windows XP registry entries that are of forensic values.
Friday, April 07, 2006
Fridays Are For Fun! - "Wow! That smarts."
A sheriff's deputy used a Taser to stop a 92-year-old man from allegedly beating his roommate with his aluminum cane at a Florida assisted living center.
Both men suffer from Alzheimer's disease, the center at Hudson, Fla., said. When struck by the Taser, Olin Holcombe's lone comment was, "Wow! That smarts."
A nurse reported hearing a "thud" shortly after midnight Thursday and she found Roland Casanova, 81, on the floor, defending himself from Holcombe's cane, the Tampa Tribune reported. The sheriff's deputy who answered the call said Holcombe swung the cane at him also before the officer drew his Taser.
"Wow! That smarts." ?! That's it? This guy's gets hit with a freekin' Taser, his pacemaker is probably vibrating faster than the toy-of-the-month on Sue Johanson's Sunday Night Sex Show, and all he says is "Wow! That smarts."
That guy is TUFF. I would've been laid out on the floor crying and wimpering, feeling something like a Mike Tyson cell mate after lights out.
A red-faced Australian nudist who tried to set fire to what he thought was a deadly funnel web spider's nest ended up with badly burnt buttocks, emergency officials said on Monday.
The 56-year-old man was at a nudist colony near Bowral, about 100 km (62 miles) southwest of Sydney, on Sunday when he spotted what he believed to be a funnel web spider hole.
Ambulance workers, including a helicopter crew, were called to the scene after the man poured petrol down the hole and then lit a match in an attempt to kill the offending arachnid.
"The exploding petrol fumes left the man with burns to 18 percent of his body, on the upper leg and buttocks," the NRMA Careflight helicopter rescue service said in a statement.
It said the man's lack of clothing probably contributed to the extent of his burns.
Tool Time - Online Pen-test tools
Wednesday, April 05, 2006
Internet Porn — Eye-Fi Commercial
The deputy press secretary for the U.S. Department of Homeland Security was charged with using a computer to seduce a child after authorities said he struck up sexual conversations with an undercover detective posing as a 14-year-old girl.
Sunday, April 02, 2006
Movie Plot Security Contest
Bruce Schneier is starting a contest:
"It is in this spirit I announce the (possibly First) Movie-Plot Threat Contest. Entrants are invited to submit the most unlikely, yet still plausible, terrorist attack scenarios they can come up with.
Your goal: cause terror. Make the American people notice. Inflict lasting damage on the U.S. economy. Change the political landscape, or the culture. The more grandiose the goal, the better.
Assume an attacker profile on the order of 9/11: 20 to 30 unskilled people, and about $500,000 with which to buy skills, equipment, etc."
You can post your movie plots on his blog here.
Saturday, April 01, 2006
Personal Security - Forget the Tinfoil Hat
ABC Suspends Producer Over Bush-Bashing E-Mail
ABC News suspended the executive producer of the weekend edition of "Good Morning America" yesterday over a pair of leaked e-mails in which he used inflammatory language to slam President Bush and Madeleine Albright.
In one of the e-mails, written during the first presidential debate in 2004 and leaked to the Drudge Report, Green wrote to a colleague on his BlackBerry: "Are you watching this? Bush makes me sick. If he uses the 'mixed messages' line one more time, I'm going to puke."
It is widely believed at ABC News that the e-mails were leaked by a former employee who has a vendetta against Green.

