Saturday, September 30, 2006
Does Crime Pay? Reselling Stolen Information
Haxdoor rootkit-equipped backdoors are widely used - in the "Rechnungen" and "Räkningen" spam runs in Germany and Sweden for example.
These changing Haxdoor variants are generated with a toolkit known as "A-311 Death".
The toolkit itself is sold on the Internet by its author, known as "Corpse" or "Korpsov".
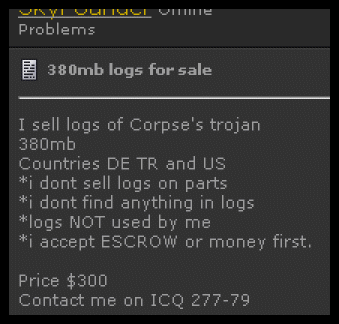
Now, people who use such backdoors quickly collect a lot of information from infected computers. Information such as passwords, credit cards, and bank logons. Some of these attackers filter the logs they collect to find juicy information and then use it themselves. Others grep the data for e-mail addresses (to sell them to spammers) and for credit card numbers and bank logins (to sell them to fraudsters).
Then again, others take the easy way out and end up selling the logs as they are, by the megabyte. Here's a screenshot from one forum:
Wednesday, September 27, 2006
Google for SQL Injection
IMMUNIZING THE INTERNET, OR: HOW I LEARNED TO STOP WORRYING AND LOVE THE WORM
An anonymous note in the Harvard Law Review argues that there is a significant benefit from Internet attacks:
This Note argues that computer networks, particularly the Internet, can be thought of as having immune systems that are strengthened by certain attacks. Exploitation of security holes prompts users and vendors to close those holes, vendors to emphasize security in system development, and users to adopt improved security practices. This constant strengthening of security reduces the likelihood of a catastrophic attack -- one that would threaten national or even global security. In essence, certain cybercrime can create more benefits than costs, and cybercrime policy should take this concept into account.
Tuesday, September 26, 2006
VR Gear Makes RC Airplane the Coolest Toy Ever
www.hak5.org - USB Password Leecher
"In this segment we'll overview a few of Microsoft Window's security weaknesses and show how to build a custom USB key that will retrieve vital information from a target computer, necessary for auditing password strength. A major flaw in the way Windows stores password information is the use of the legacy LM, or LAN Manager hash. While this hash is based on DES encryption it is vulnerable to time-memory trade-off attacks due to it's poor implementation. Our custom USB key uses new U3 technology to automatically and invisibly retrieve these weak hashes within seconds of being inserted into the target computer. From here the LM hashes can be tested against a set of rainbow tables using the popular rainbowcrack software and audited for password strength. We will also cover password best practices and prevention methods for this type of attack."
Episode 2×02 Release
Saturday, September 23, 2006
Friday, September 22, 2006
Fridays are for Fun - Securing World Peace
Sunday, September 17, 2006
WirelessDefender.net
 A support site for the Wireless Defender knuckleheads, with a community that is busy hacking on UsbWiSec.
A support site for the Wireless Defender knuckleheads, with a community that is busy hacking on UsbWiSec. http://www.wirelessdefender.net
Gone Phishing...
Scam artists using fake e-mails purportedly from Fifth Third Bank have stolen $163,000 from the Northern Kentucky Chamber of Commerce's bank accounts. It's the highest-profile case since the Cincinnati bank - the nation's 11th-largest - became a target for "phishing" scams this summer. Phishing is the act of tricking someone into giving confidential information or tricking them into doing something they normally wouldn't. Crooks typically use banks' and other financial-services companies' IDs because of their large customer bases. According to the anti-virus company McAfee, Fifth Third made up 60.5 percent of all phishing attacks in August. Working with the FBI, the chamber has recovered $65,465 and has traced $43,541 more that is pending recovery. Chamber president Steve Stevens said in a news release that the chamber is financially stable.
Kevin Mitnick on NPR (audio)
Tuesday, September 12, 2006
NetCat Tips - Quiet Exploration of Ports
We all know about netcat, so I won't do an introduction about it. Instead I will talk about the use of netcat in the quiet exploration of ports. As Netcat can talk with a range of ports, an obvious use for it will be to use it as ports' explorer. The first impulse is to connect Netcat to a complete range of ports on the target system.
[root@peruvian nc]# ./nc target 20 - 80
This will not work. Remember that Netcat is not a port scanner. In this situation, Netcat will start at port 80 and will try to carry out TCP connections to any ports that respond. As soon as it receives an answer on a port, Netcat will wait for a standard response before continuing. This Behavior is not the one that we are looking for.
The option -z is the answer. This option will tell Netcat to send a minimum amount of data to obtain an answer from an open port. When the -z switch is used netcat will not be able to send data to the remote port and as soon as the port is open it is immediately shutdown and closed. This allows us to avoid waiting for a response before continuing.
The verbose switch (option -v) provides details on the connections that Netcat is carrying out so will be able to use this to see the results of its analysis of the ports. Without this option,… well…, it will not be able to see anything. An example follows next:
[root@peruvian nc]# ./nc -z 192.168.1.100 20-80
[root@peruvian nc]# ./nc -v -z 192.168.1.100 20-80
peruvian [192.168.1.100] 80 (www) open
peruvian [192.168.1.100] 23 (telnet) open
peruvian [192.168.1.100] 22 (ssh) open
peruvian [192.168.1.100] 21 (ftp) open
[root@peruvian nc]#
When using the -v switch, we can see the status of the ports of some of the usual services running on the remote machine. What will our scan look like in the logs of the target system?
July 16 16:15:12 peruvian sshd[21690] : Did not receive ident string from 192.168.1.105
July 16 16:15:12 peruvian telnetd[21689] : ttloop: read: Broken pipe
July 16 16:15:12 peruvian ftpd[21691] : FTP session closed
We see that traces of our activity have been left on the target system. The system tracks the moment we scanned and the list of consecutive processes (21689 to 21691) we explored. If we had scanned a greater range of ports it would have left a really huge track in the logs of the target system. Also certain services, for example sshd, are so bad-mannered that they will save the IP address of the scanner.
Even if we scan a port on which nothing is running (and therefore the connection will not be logged), most networks count on intrusión detection systems that will immediately indicate this type of malicious behavior and they will call the attention of the administrator. Some Firewall applications will also block an IP address automatically if they receive too many connections on in a brief period of time.
Netcat allows the execution of a more sophisticated way to avoid this :D. We will be able to use option -i and to form a test interval. It will take a little more time to obtain the data, but the exploration with this allows more events to happen between each connection to help keep us off of the radar.
If we use the option -r so that Netcat explores of random form these ports, this process will look even less like an exploration of ports:
./nc -v -z -r -i 42 192.168.1.100 20-80
The previous instruction tells Netcat to choose a random range of ports between positions 20 and 80 in the 192.168.1.100 address and to try to connect to each one of them every 42 seconds. This method should bypass any automated defensive system, but the evidence of the exploration will continue to exist in the registries of the target system; they will only be more disordered.
You can also use netcat to carry out a quiet exploration of ports using UDP. All you need to do is add the -u option to instruct netcat to explore UDP instead of TCP ports.
*Note1:
Scanning with the UDP protocal has a problem. Netcat depends on the reception of an Internet Control Mensajes Protocol (ICMP) to determine if a UDP port is open or closed. If the ICMP is being blocked by a Firewall or a filter, Netcat will falsely report that these UDP ports are open.
Netcat is not a very sophisticated port scanner. One of its main features is that it is a very good general tool and does not emphasize any specialty. For this reason it is better to use a specifically developed port analyzer.
*Note2:
If you're getting errors when trying to port scan, try to limit netcat to a specific IP address and a specific port by using the -s and -p switches. Choose a port below 1024 or a port that isn't used by any service.
More questions:
----------------------
root3d
system666x@gmail.com
Perú [16/07/2006]
16:44
----------------------
Personal Security - Wear A Bike Helmet, Get Hit!
 Cyclists who wear helmets are more likely to be knocked down by passing vehicles, research suggests.
Cyclists who wear helmets are more likely to be knocked down by passing vehicles, research suggests. A study found that drivers tended to pass closer when overtaking cyclists wearing helmets than those who were bareheaded, by 8.5cm on average.
Saturday, September 09, 2006
Monday, September 04, 2006
Saturday, September 02, 2006
The "Janus Project"
 The "Janus Project" is the brainchild of Kyle Williams of the Janus Wireless Security Research Group in Portland, Oregon.
The "Janus Project" is the brainchild of Kyle Williams of the Janus Wireless Security Research Group in Portland, Oregon.Mounted inside an epoxy and silicone-sealed watertight case lives a 1.5GHz C7 powered EPIA EN 15000G motherboard, 2 x four-port PCI to mini-PCI adapters, 8 x 802.11a/b/g mini-PCI WLAN Modules, 2 x 1W 2.4Ghz WLAN amplifiers, a keyboard and a 17in LCD screen. The system can scan up to 300 wireless networks simultaneously, storing and AES encrypting in real time all the data onto its 20GB hard drive.

By focusing all 8 WLAN cards onto an access point and using a combination of common Linux tools, the Janus Project can crack a WEP key in under 5 minutes. WPA and WPA2 encryption aren't far behind - Kyle and his friend Martin Peck are optimising the software to use the Padlock hardware acceleration of the C7 chip to crack those too.
If Kyle gets captured in enemy territory and tortured, an "Instant Off" switch will render the captured data useless until a password is entered and a USB stick containing a 2000-bit passkey is inserted. Presumably during the torturing process.
Friday, September 01, 2006
Friday Fun - Burning Man 2006 TV
 Burning Man 2006 is now in full swing and Current TV has setup an online television station, TV Free Burning Man.
Burning Man 2006 is now in full swing and Current TV has setup an online television station, TV Free Burning Man.They have been shooting video, doing interviews and uploading a daily show from Black Rock City. They will be doing a live broadcast the burn on Saturday night (September 2nd) starting at 9 PM PST/12 AM EST.



