Friday, April 28, 2006
The Use by Banks of Non-SSL Login Forms
Fridays are for Fun - Judge creates own Da Vinci code
 Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.
Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.Seemingly random italicized letters were included in the 71-page judgment given by Mr Justice Peter Smith, which apparently spell out a message.
Mr Justice Smith said he would confirm the code if someone broke it.
"I can't discuss the judgment, but I don't see why a judgment should not be a matter of fun," he said.
You can check it out for yourself here.
Thursday, April 27, 2006
Security Myths and Passwords
Policies requiring regular password changes (e.g., monthly) are an example of exactly this form of infosec folk wisdom.
From a high-level perspective, let me observe that one problem with any widespread change policy is that it fails to take into account the various threats and other defenses that may be in place. Policies should always be based on a sound understanding of risks, vulnerabilities, and defenses. “Best practice” is intended as a default policy for those who don’t have the necessary data or training to do a reasonable risk assessment.
Tuesday, April 25, 2006
Tool Time - Cmos password recovery tools 4.8
Works with the following BIOSes
* ACER/IBM BIOS
* AMI BIOS
* AMI WinBIOS 2.5
* Award 4.5x/4.6x/6.0
* Compaq (1992)
* Compaq (New version)
* IBM (PS/2, Activa, Thinkpad)
* Packard Bell
* Phoenix 1.00.09.AC0 (1994), a486 1.03, 1.04, 1.10 A03, 4.05 rev 1.02.943, 4.06 rev 1.13.1107
* Phoenix 4 release 6 (User)
* Gateway Solo - Phoenix 4.0 release 6
* Toshiba
* Zenith AMI
With CmosPwd, you can also backup, restore and erase/kill cmos.
Cain & Abel v2.8.9 released
- Added hashes syncronization functions (Export/Import) to/from Cain for PocketPC via ActiveSync.
- Added VoIP sniffer support for the following codecs: G723.1, G726-16, G726-24, G726-32, G726-40, LPC-10.
- Added support for Winpcap v3.2.
Download here.
Monday, April 24, 2006
Home Security - Man dies when large hole opens in home
Full story here.It was like a scene from a horror film: A 27-year-old man plummeted into a gaping hole that suddenly opened beneath a house, trapping him beneath foundation rubble and killing him.
"It's unbelievable," Placer County Sheriff's Department spokeswoman Dena Erwin said. "From the front of the house, it's absolutely normal. Then, in the middle of the house, is this enormous hole."
The victim was awake and on the ground floor about 9:30 p.m. Friday when the concrete foundation near the kitchen gave way, sending him plunging into to the ground, Erwin said.
Saturday, April 22, 2006
Super-Glue: Best practice for countering key stroke loggers

Read all the details in this article.
The one thing not mention in the article is that it is reported that Sumitomo Bank's best practice for avoiding a repeat attack is that they now super-glue the keyboard connections into the backs of their PCs.
Tuesday, April 18, 2006
Image stealing by phishers
From F-Secure Blog...
Lazy phishers are often simply making a copy of the original bank site with some malicious modifications. As an example, take a look at this currently active phishing site targeting Chase Bank.
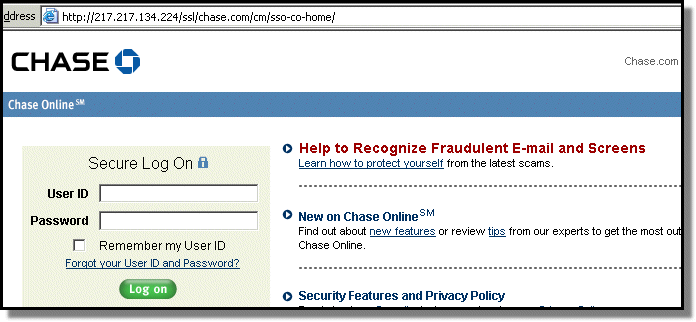
This phishing site is running on an infected home computer in Spain. Only the html is hosted there; all the images are actually loaded directly from a real chase.com server.
Now, activity like this could be detected by the website of the bank automatically. How about modifying the logic of the bank web server to do something along these lines:
If somebody
a) loads my images but
b) does not load the corresponding html file and
c) has http referrer -values outside of my domain
then, for this user, lets change this image:
to this image:

This could be activated only after the activity has happened from, say, 10 different IP addresses, to make it harder for the attackers to spot it until it's too late.
And, in most cases the REFERRER fields would directly point the bank staff to the real phishing site which they could now start closing down.
Eventually, attackers would move to host their own images, but for now they still typically don't.
Monday, April 17, 2006
Triple-DES Upgrade Adding Insecurities?
In a press release today, Redspin, an independent auditing firm based in Carpinteria, CA, suggests that the recent mandated upgrades of ATMs to support triple DES encryption of PINs has introduced new vulnerabilities into the ATM network environment - because of other changes that were typically made concurrently with the triple DES upgrades.
Sunday, April 16, 2006
Personal Security - So... You Think the Cold War is Over?
In a rare news conference, the designer of Russia's intercontinental ballistic missiles dismissed on Thursday a warning that Russia was falling behind the United States in the number of active nuclear warheads it has and said his Topol-M and Bulava missiles would serve as a sufficient deterrent until at least 2040.
"I assure you that the number of active warheads the strategic nuclear forces will have in 2015 and even in 2020 will be no less than 2,000," said Yury Solomonov, head and chief designer at the Moscow Institute of Thermal Technology, Russia's leading designer of intercontinental missiles.
Saturday, April 15, 2006
US Military Buys Back Stolen Flash Drives from Afghan Shopkeepers
Maps, charts, and intelligence reports on computer drives smuggled out of a US base and sold at a local bazaar describe how Taliban and Al Qaeda leaders have been using southwestern Pakistan as a key planning and training base for attacks in Afghanistan.
The documents, marked ''secret," appear to be raw intelligence reports based on conversations with Afghan informants, and official briefings given to high-level US military officers. Together, they outline how the US military came to focus its search for members of Taliban, Al Qaeda, and other terrorist groups on the border region with Pakistan and Pakistani territory.
American investigators have paid thousands of dollars to buy back the stolen drives, according to shopkeepers outside the major military base here, but many were still on sale yesterday.
Included on some drives were the Social Security numbers of hundreds of US soldiers, including four generals, and lists of troops who completed nuclear, chemical, and biological warfare training, the Associated Press reported.
Wednesday, April 12, 2006
Saturday, April 08, 2006
Forensic Analysis of the Windows Registry
Windows registry contains lots of information that are of potential evidential value or helpful in aiding forensic examiners on other aspects of forensic analysis. This paper discusses the basics of Windows XP registry and its structure, data hiding techniques in registry, and analysis on potential Windows XP registry entries that are of forensic values.
Friday, April 07, 2006
Fridays Are For Fun! - "Wow! That smarts."
A sheriff's deputy used a Taser to stop a 92-year-old man from allegedly beating his roommate with his aluminum cane at a Florida assisted living center.
Both men suffer from Alzheimer's disease, the center at Hudson, Fla., said. When struck by the Taser, Olin Holcombe's lone comment was, "Wow! That smarts."
A nurse reported hearing a "thud" shortly after midnight Thursday and she found Roland Casanova, 81, on the floor, defending himself from Holcombe's cane, the Tampa Tribune reported. The sheriff's deputy who answered the call said Holcombe swung the cane at him also before the officer drew his Taser.
"Wow! That smarts." ?! That's it? This guy's gets hit with a freekin' Taser, his pacemaker is probably vibrating faster than the toy-of-the-month on Sue Johanson's Sunday Night Sex Show, and all he says is "Wow! That smarts."
That guy is TUFF. I would've been laid out on the floor crying and wimpering, feeling something like a Mike Tyson cell mate after lights out.
A red-faced Australian nudist who tried to set fire to what he thought was a deadly funnel web spider's nest ended up with badly burnt buttocks, emergency officials said on Monday.
The 56-year-old man was at a nudist colony near Bowral, about 100 km (62 miles) southwest of Sydney, on Sunday when he spotted what he believed to be a funnel web spider hole.
Ambulance workers, including a helicopter crew, were called to the scene after the man poured petrol down the hole and then lit a match in an attempt to kill the offending arachnid.
"The exploding petrol fumes left the man with burns to 18 percent of his body, on the upper leg and buttocks," the NRMA Careflight helicopter rescue service said in a statement.
It said the man's lack of clothing probably contributed to the extent of his burns.
Tool Time - Online Pen-test tools
Wednesday, April 05, 2006
Internet Porn — Eye-Fi Commercial
The deputy press secretary for the U.S. Department of Homeland Security was charged with using a computer to seduce a child after authorities said he struck up sexual conversations with an undercover detective posing as a 14-year-old girl.
Sunday, April 02, 2006
Movie Plot Security Contest
Bruce Schneier is starting a contest:
"It is in this spirit I announce the (possibly First) Movie-Plot Threat Contest. Entrants are invited to submit the most unlikely, yet still plausible, terrorist attack scenarios they can come up with.
Your goal: cause terror. Make the American people notice. Inflict lasting damage on the U.S. economy. Change the political landscape, or the culture. The more grandiose the goal, the better.
Assume an attacker profile on the order of 9/11: 20 to 30 unskilled people, and about $500,000 with which to buy skills, equipment, etc."
You can post your movie plots on his blog here.
Saturday, April 01, 2006
Personal Security - Forget the Tinfoil Hat
ABC Suspends Producer Over Bush-Bashing E-Mail
ABC News suspended the executive producer of the weekend edition of "Good Morning America" yesterday over a pair of leaked e-mails in which he used inflammatory language to slam President Bush and Madeleine Albright.
In one of the e-mails, written during the first presidential debate in 2004 and leaked to the Drudge Report, Green wrote to a colleague on his BlackBerry: "Are you watching this? Bush makes me sick. If he uses the 'mixed messages' line one more time, I'm going to puke."
It is widely believed at ABC News that the e-mails were leaked by a former employee who has a vendetta against Green.
Friday, March 31, 2006
(IN)SECURE Magazine Issue1.6 (March 2006)
The covered topics are:
- Best practices in enterprise database protection
- Quantifying the cost of spyware to the enterprise
- Security for websites - breaking sessions to hack into a machine
- How to win friends and influence people with IT security certifications
- The size of security: the evolution and history of OSSTMM operational security metrics
- Interview with Kenny Paterson, Professor of Information Security at Royal Holloway, University of London
- PHP and SQL security today
- Apache security: Denial of Service attacks
- War-driving in Germany - CeBIT 2006
Tool Time - Ophcrack 2.2 Is Out
Thursday, March 30, 2006
The Code Room: Breaking Into Vegas
 In this episode of The Code Room watch the White Hats and Black Hats battle for the security of Las Vegas. Jessi Knapp and Microsoft Security Guru Joe Stagner narrate as the Hackers try to gain control of The Plaza's online money management system and our Security Team tries to stay one step ahead
In this episode of The Code Room watch the White Hats and Black Hats battle for the security of Las Vegas. Jessi Knapp and Microsoft Security Guru Joe Stagner narrate as the Hackers try to gain control of The Plaza's online money management system and our Security Team tries to stay one step ahead
Harvard and Berkley Study: Why Phishing Works
Tuesday, March 28, 2006
Firefox Bug Causes Breakup with Fiancé
 Sure blame the browser. The bug report makes for a fun read...
Sure blame the browser. The bug report makes for a fun read...How this particular privacy issue ended up in a relationship breakdown emerges from the bug report. The website designer that submitted the report writes that she had changed her mind when Firefox asked whether it should save the password for her website and dived into Password Manager to change her preference. What she found when she got there were the preferences of her fiancé: a list of dating and swinging websites that he had set to explicitly, and understandably, never save a password for…
News story here.
Hack Into Touch-Screen Voting Machine (undetected) and Win 10K!
Dr. Shamos, a professor of computer science at Carnegie Mellon University who has spent more than two decades testing electronic voting equipment, first made that offer several years ago. To this day, no one has tried to collect.
"Because they know they can't do it," he said last week.
Phishing With A New Twist
Not so for the attack on Capital City Bank, Wakulla Bank and Premier Bank in northern Florida. On March 14 hackers were able to break into the servers of ElectroNet, a Tallahassee, Fla. service provider which hosted the web sites for all three banks. The main business URL for the banks' were redirected to identical spoof sites on offshore servers, which asked customers to provide their login details.
The intrusion was detected about an hour after it started, ElectroNet CEO Allen Byington told the Tallahassee Democrat. Byington said that ElectroNet stores no confidential data on its computers and that the company was "working closely" with law enforcement agencies investigating the incident. The banks' sites were shut down for several days, and bank officials said the financial losses were "minimal," and that any customers who lost money were reimbursed by their respective banks.
Monday, March 27, 2006
Tool Time - EtherFlood
EtherFlood might be your answer. EtherFlood floods a switched network with Ethernet frames with random hardware addresses. The effect on some switches is that they start sending all traffic out on all ports so you can sniff all traffic on the network.
Details here.
You Are What You Post
Companies are increasingly googling the names of employees and potential employees to dig up information on them. Is what one finds on google an accurate representation of a person? What would your next boss find?
Saturday, March 25, 2006
Personal Security - Disney Film about Venereal Diseases
 Originally Released in 1973
Originally Released in 1973A general addressing his troops, which happen to be syphilis and gonorrhea germs. There are also characters representing ignorance and fear.
This is an educational short produced at the Walt Disney Studios.
Friday, March 24, 2006
In the News - SourceFire has been DPW'd. (Dubai Port World-ed)
From the Fridays Are For Fun Archives - You're In Control
 The You're In Control system uses an array of piezoelectric sensors mounted to the back of a urinal to detect the position of a stream of water, allowing a person to play a video game while peeing. A video monitor is mounted above the urinal, and position on the back of the urinal corresponds to position on the screen. We created a custom video game (our interpretation of the carnival game "whack-a-mole") in which the player attempted to hit hamsters as they flew out of one hole and into another hole in the ground. A successful hit would turn the hamster yellow, make it scream and spin out of control, and give the player ten points.
The You're In Control system uses an array of piezoelectric sensors mounted to the back of a urinal to detect the position of a stream of water, allowing a person to play a video game while peeing. A video monitor is mounted above the urinal, and position on the back of the urinal corresponds to position on the screen. We created a custom video game (our interpretation of the carnival game "whack-a-mole") in which the player attempted to hit hamsters as they flew out of one hole and into another hole in the ground. A successful hit would turn the hamster yellow, make it scream and spin out of control, and give the player ten points.IBM Demos ‘chip on a molecule’
 The first computer circuit to be built on a single molecule has been unveiled by researchers in the US.
The first computer circuit to be built on a single molecule has been unveiled by researchers in the US.It was assembled on a single carbon nanotube, a standard component of any nanotechnologist's toolkit.
The circuit is less than a fifth of the width of a human hair and can only be seen through an electron microscope.
The researchers, from IBM and two US universities in Florida and New York, told the journal Science that the work could lead to faster computer chips.
Wednesday, March 22, 2006
Firefox 2.0 Alpha Download
Download here.
Control your PC from an IRC room
You might find some other fun stuff on the related site - Script is here.
Monday, March 20, 2006
Cybersafety Campaign for Preschoolers Launched
Parents have more to worry about than their child grazing their knee in the playground -- they now should be concerned their toddlers are being kept "cybersafe" as well, an internet safety group said today.
A campaign to keep preschoolers safe when playing on the internet and with other modern technology is to be launched this week.
"In addition to young children inadvertently finding inappropriate material or being exposed to online predators and cyber bullies, they observe and copy the online behaviour of their parents and older siblings to an extent often not realised by their families," Ms Balfour said.
She cited the example of a New Zealand family that was surprised to receive a parcel of videos ordered online by their four-year-old.
"This experience just goes to show how well youngsters can copy behaviour."
"Young children may appear skilled in internet use, but they will not have yet developed the understanding and judgment to always keep themselves cybersafe," Ms Balfour said.
Sunday, March 19, 2006
Geo IP Tool
Computer Networks: The Heralds of Resource Sharing
Saturday, March 18, 2006
Some Cool USB Toys
 Not meant to be a product plug, but these folks have some cool stuff...
Not meant to be a product plug, but these folks have some cool stuff...PC on a USB Stick Fights Child Pornography
The US 9th Circuit of Appeals recently made a ruling to allow police to search computer hard drives for child pornography if the PC owner is found to have subscribed to sites selling illegal images. To search a PC without knowing the password, the police can now turn to the Computer on a Stick Pro (COS).
The COS is a USB drive its own bootable operating system. To use it the police simply plug the COS into a vacant USB port on the suspect computer and allow the PC to reboot using the COS operating system, bypassing Windows passwords. Once booted the COS allows the files on the attached computer system to be viewed and copied to the USB COS hard drive.
Microsoft BlueHat Security Briefings Online
Friday, March 17, 2006
Shmoocon 2006 Follow-Up
 Badges: The ShmooCon 2006 Badges were made of Stainless Steel. Some people thought the badges were a bit dangerous, but they were quite tame compared to the original design. There were 20 different badge designs, including Speaker, Staff, Shmoo & Attendee. Finding a complete set to put the puzzle together took a bit of work and the prize went to Grey Frequency who met over 200 attendees and traced badges to put it all together.
Badges: The ShmooCon 2006 Badges were made of Stainless Steel. Some people thought the badges were a bit dangerous, but they were quite tame compared to the original design. There were 20 different badge designs, including Speaker, Staff, Shmoo & Attendee. Finding a complete set to put the puzzle together took a bit of work and the prize went to Grey Frequency who met over 200 attendees and traced badges to put it all together.Video: Finally starting to get some movies online... Check out the speaker list to see if the movie you're looking for is online yet. They will be posting about 5 movies a day. Hopefully in a week or so they'll all be online.
Thursday, March 16, 2006
A Good List of Live CD Distributions
Wednesday, March 15, 2006
Secure Voice over IP: Zfone
Tuesday, March 14, 2006
Tool Time - USB, FireWire and PCMCIA Scanner

Monday, March 13, 2006
The Bookmaker, the Wiz Kid and the Extortionist
Saturday, March 11, 2006
Ubuntu
Among the other public commitments the Ubuntu team makes, the team promises that the operating system will always be free, and there will be a new release every six months (each release is supported for 18 months).
More info and download here.
Prisoner 151716 of Cellblock 1A
 Under the government of Saddam Hussein, Mr. Qaissi was a mukhtar, in effect a neighborhood mayor, a role typically given to members of the ruling Baath Party and closely tied to its nebulous security services. After the fall of the government, he managed a parking lot belonging to a mosque in Baghdad.
Under the government of Saddam Hussein, Mr. Qaissi was a mukhtar, in effect a neighborhood mayor, a role typically given to members of the ruling Baath Party and closely tied to its nebulous security services. After the fall of the government, he managed a parking lot belonging to a mosque in Baghdad.He was arrested in October 2003, he said, because he loudly complained to the military, human rights organizations and the news media about soldiers' dumping garbage on a local soccer field. But some of his comments suggest that he is at least sympathetic toward insurgents who fight American soldiers.
"Resistance is an international right," he said.
Weeks after complaining about the garbage, he said, he was surrounded by Humvees, hooded, tied up and carted to a nearby base before being transferred to Abu Ghraib. Then the questioning began.
Read the full story here.
Friday, March 10, 2006
Computer Security Awareness Video Contest Winners
The EDUCAUSE/Internet2 Computer and Network Security Task Force and the National Cyber Security Alliance would like to announce the winners of a computer security awareness video contest, which was held as part of a national campaign to raise awareness of and increase computer security at colleges and universities. The contest searched for two categories of short computer awareness videos that addressed a broad range of security topics or focused on a single security issue. Submissions were developed by college students for college students. The winning videos are featured here and will be used in campus security awareness campaigns and efforts.
The contest included 62 video submissions from 17 universities. Winners were selected for creativity, content, and quality of information; overall effectiveness of delivery; and technical quality. Cash prizes were awarded to winners in each category. The two gold winners received $1,000, the two silver winners received $800, and the two bronze winners received $500 in cash prizes. For additional information, please see the press release.
See the winners here.
Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text.info
Title says it all...
Happy Friday
ABA Journal - Stolen Lives
Wednesday, March 08, 2006
The Analog Hole
I try to avert my eyes when the person sitting next to me on the plane opens a laptop and displays a confidential memo. It may have been transmitted over a secure link (though it probably wasn’t), and it may be encrypted on disk (though it probably isn’t), but there it is in plain view, pouring out of the analog hole.
SecurityForest.com
Sunday, March 05, 2006
Live Action Recreation of the intro to The Simpsons
Saturday, March 04, 2006
Online Amateurs Crack Nazi Codes
 Three German ciphers unsolved since World War II are finally being cracked, helped by thousands of home computers. The codes resisted the best efforts of the celebrated Allied cryptographers based at Bletchley Park during the war. Now one has been solved by running code-breaking software on a "grid" of internet-linked home computers.
Three German ciphers unsolved since World War II are finally being cracked, helped by thousands of home computers. The codes resisted the best efforts of the celebrated Allied cryptographers based at Bletchley Park during the war. Now one has been solved by running code-breaking software on a "grid" of internet-linked home computers.More info here.
Friday, March 03, 2006
Fun with Stored Value Cards
Hydra - A very fast Network Logon Cracker
Number one of the biggest security holes are passwords, as every password security study shows.
Hydra is a parallized login cracker which supports numerous protocols to attack. New modules are easy to add, beside that, it is flexible and very fast.
Currently this tool supports:
TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA (incorporated in telnet module).
This tool is a proof of concept code, to give researchers and security consultants the possiblity to show how easy it would be to gain unauthorized access from remote to a system.
Friday Fun - Jon Stewart on Larry King
In case you missed Jon Stewart on Larry King the other night, Crooks & Liars has video and a partial transcript (but you really need to see or hear it, because a lot of the way Jon Stewart talks is lost in the literal written tranlsation.) Larry King made several feeble attempts to create controversy, and Jon Stewart kicked him square in the nuts each time. Witness this exchange:
KING: You don't want Medicare to fail?
STEWART: Are you insane?
KING: No.
STEWART: You're literally asking me if I would prefer -- yes, Larry, what I'm saying to you as a comedian I want old people to suffer, old and poor people to suffer. That is -- that is -- what we want is -- what seems absurd to me is the length that Washington just seems out of touch with the desires of Americans to be spoken to as though they are adults.
Nice try, Larry; too bad Jon didn't go for it. Maybe you can team up with Nancy Grace for a two hour Aruba Special to get back on familiar, more comfortable ground.
That question was just one of several "gotcha" attempts which failed spectacularly when Jon refused to take the bait, and instead turned the ludicrous question back on Larry King, who of course had no response other than this painful frozen half-smile that was equal parts fear and lothing. When Larry King wasn't completely controlling the tone and content of the show, you could feel how uncomfortable he was. Jon Stewart was so funny, and so quick-witted, and so smart and so insightful, if Larry King wasn't trying so hard to create controversy where there was none, you'd almost feel bad that he wasn't able to keep up.
Thanks to WWdNWednesday, March 01, 2006
Security Awareness Tips from DHS/US-Cert
Simpsons 'trump' First Amendment
 This is from a BBC story... Nice to see how they see us across the pond...
This is from a BBC story... Nice to see how they see us across the pond...Only one in four could name more than one of the five freedoms it upholds but more than half could name at least two members of the cartoon family.
About one in five thought the right to own a pet was one of the freedoms.
Monday, February 27, 2006
Cell Gunphone
 Here a one for the "What were they thinking file"...
Here a one for the "What were they thinking file"...At first sight it looks like a regular cell phone — same size, same shape, same overall appearance.
But beneath the digital face lies a .22-caliber pistol, a phone gun capable of firing four rounds in quick succession with a touch of the otherwise standard keypad.
The US Department of Homeland Security and the FBI are aware of the device and have instructed baggage screeners to be on the lookout for suspicious mobile phones. This is especially after 9/11.
European law enforcement officials — stunned by the discovery of these deadly decoys — say phone guns are changing the rules of engagement in Europe.
Airport authorities across Europe are implementing systems to X-ray all cell phones
“We find it very, very alarming,” says Wolfgang Dicke of the German Police union. “It means police will have to draw their weapons whenever a person being checked reaches for their mobile phone.”
The FBI, the Bureau of Alcohol, Tobacco and Firearms, and the U.S. Customs Service say they’ve been briefed on the new weapons.
“This criminal invention represents a potentially serious threat to law enforcement and the public,” said U.S. Customs Service Commissioner Raymond W. Kelly.
“We received word about these guns last month. We have since alerted our field personnel to be on the lookout for ‘cell phone guns’ at U.S. ports of entry.”
Full story and video here.
Rootkit Pharming
Sunday, February 26, 2006
E&Y Loses Four more Laptops
This theft follows a higher-profile incident earlier this month in which an Ernst and Young employee lost his laptop containing the social security numbers and other personal information of customers.
Ernst and Young appears set on establishing a laptop loss record in February...
Episode Six of the Sysadmin Sitcom The IT Crowd is now Downloadable
 Episode six of Graham Linehan's wonderful, screamingly funny sysadmin sitcom, The IT Crowd, is online here.
Episode six of Graham Linehan's wonderful, screamingly funny sysadmin sitcom, The IT Crowd, is online here.
Saturday, February 25, 2006
DIY Hardware keylogger
 Looking for that extra special DIY project this weekend? Here's how to make a PS/2 keyboard line keylogger, also provided - the software application with full source code to download the recorded data.
Looking for that extra special DIY project this weekend? Here's how to make a PS/2 keyboard line keylogger, also provided - the software application with full source code to download the recorded data.DoD Staffer's Notes from 9/11 Obtained Under FOIA
"Hard to get good case. Need to move swiftly," the notes say. "Near term target needs - go massive - sweep it all up, things related and not."
The handwritten notes, with some parts blanked out, were declassified this month in response to a request by a law student and blogger, Thad Anderson, under the US Freedom of Information Act. Anderson has posted them on his blog at outragedmoderates.org.
Friday, February 24, 2006
New technique uses Photons, Physics to Foil Codebreakers
For governments and corporations in the business of transmitting sensitive data such as banking records or personal information over fibre optic cables, a new system demonstrated by University of Toronto researchers offers the protective equivalent of a fire-breathing dragon.
“Quantum cryptography is trying to make all transmissions secure, so this could be very useful for online banking, for example,” says Professor Hoi-Kwong Lo, an expert in physics and electrical and computer engineering at U of T’s Centre for Quantum Information and Quantum Control and the senior author of a new study about the technique. “The idea can be implemented now, because we actually did the experiment with a commercial device.”
The study describes the first experimental proof of a quantum decoy technique to encrypt data over fibre optic cable. In quantum cryptography, laser light particles (photons) carry complex encryption keys through fibre optic cables, dramatically increasing the security of transmitted data. Conventional encryption is based on the assumed complexity of mathematical problems that traditional computers can solve. But quantum cryptography is based on fundamental laws of physics — specifically, Heisenberg’s Uncertainty Principle, which tells us that merely observing a quantum object alters it.
Thursday, February 23, 2006
Taser Sets Florida Man On Fire
A man in Daytona Beach, Fla., was injured when a probe from a police Taser gun hit a butane lighter in his pocket and set him on fire, according to a Local 6 News report.
Police said Dennis Crouch, 54, apparently stabbed himself inside his home located in the 400 block of Grandview Avenue.
When officers arrived at the house, they found Crouch with a butcher knife threatening to kill himself.
Crouch apparently refused to comply with officers demands and was shot with a Taser gun.
A Taser probe hit a disposable butane lighter in his shirt pocket and ignited. Officers then rolled him to the ground to put out the flames.
Crouch was treated at Halifax Medical Center for burns and the stab wound.
The incident is under investigation to determine if additional safety requirements, Local 6 News reported.
[Full-disclosure] Gay Security Industry Experts Exposed!
Wednesday, February 22, 2006
Mini-Pentoo 2006.0 - Pentoo LiveCD Security Disk
 This version is only 186 Mb fat and fits on mini-cd and 256 MB usb pen-drive.
This version is only 186 Mb fat and fits on mini-cd and 256 MB usb pen-drive.It features the bare minimum tools for pentesting and support modules addition ala slax, allowing you to add some more stuff as you see fit.
You can also save your /etc, /root, ExploitTree and Nessus on a usb pen-drive, or anywhere else you want.
And last but not least, the Window Manager is the most sexiest available in the universe, providing you with genuine pen-testing pleasure.
DOWNLOAD
Download MPentoo LiveCD (HTTP).
Download MPentoo LiveCD (FTP).
Court Ruling Regarding Gramm-Leach-Bliley
In a legal decision that could have broad implications for financial institutions, a court has ruled recently that a student loan company was not negligent and did not have a duty under the Gramm-Leach-Bliley statute to encrypt a customer database on a laptop computer that fell into the wrong hands. Intrigued? Read on.
The judge dismissed the lawsuit. And then he noted...
Significantly, while recognizing that Gramm-Leach-Bliley does require financial institutions to protect against unauthorized access to customer records, Judge Kyle held that the statute "does not prohibit someone from working with sensitive data on a laptop computer in a home office," and does not require that "any nonpublic personal information stored on a laptop computer should be encrypted."
Tuesday, February 21, 2006
Secure Flying - Tuesdays Can Be For Fun Sometimes!
 Simple but a tad addictive. You must carefully pilot the helicopter,
Simple but a tad addictive. You must carefully pilot the helicopter,avoiding the obstacles...
Click on the pic to begin!
Monday, February 20, 2006
A True Story: "How we caught an Identity Thief"
It all started with a phone call. "Someone has the likeness of our site, on a very similar sounding domain!" This is the story of how igxglobal worked in conjunction with the client and the FBI to identify and stop a would be Identity thief.
Sunday, February 19, 2006
Personal Security - Severed Arm Still Clutching Mobile Phone
Jacqueline Dotson and her six-year-old daughter had to be cut out of their vehicle after the accident in which Dotson veered into the median and over-corrected, rolling her truck over the guardrail and landing upside down after flipping several times.
Several people stopped to help, and it turns out, the good samaritans may very well have saved Dotson's life. Sheila Vice, a nurse's aide, and an off-duty EMT from another county stopped to help, and put a tourniquet on Dotson's arm to stop the bleeding. Her arm was found near the accident still clutching a cell phone.
"Basically we stayed there and talked to them until the EMT drivers got there," said Vice.
Rescuers used the jaws of life to get the Dotson and her daughter out of the truck. Both were flown to hospitals, and Dotson is listed in serious condition at UK Hospital. Her daughter is not in the hospital, and sheriff's officials say they believe she's going to be fine.
Both were wearing seat belts.
Saturday, February 18, 2006
New episode of The IT Crowd, Very Cool SysAdmin Sitcom
Building a Forensics Computer
 Not a ton of info, but here is a link to an interesting article on building a 'forensics computer' used for analyzing compromised machines and security research. Fun Stuff...
Not a ton of info, but here is a link to an interesting article on building a 'forensics computer' used for analyzing compromised machines and security research. Fun Stuff... Friday, February 17, 2006
Friday Fun - Video Game Nostalgia
 If you're a 1980s game geek, you could easily spend an entire day at this website, which has a comprehensive history of video games, beginning in the years that preceded Pong, and heading all the way up to the Vectrex/Atari 7800 years. The whole site is wonderfully put together, with old adverts, screen shots, and pictures of consoles, machines and designers.
If you're a 1980s game geek, you could easily spend an entire day at this website, which has a comprehensive history of video games, beginning in the years that preceded Pong, and heading all the way up to the Vectrex/Atari 7800 years. The whole site is wonderfully put together, with old adverts, screen shots, and pictures of consoles, machines and designers.I have a Pong game like this. Ah the memories...
Thursday, February 16, 2006
Personal Security - US and Canadian Skiers get Smart Armour
The lightweight bendable material, known as d3o, can be worn under normal ski clothing. It will provide protection for US and Canadian skiers taking part in slalom and giant slalom races in Turin, Italy. Skiers normally have to wear bulky arm and leg guards to protect themselves from poles placed along the slalom run.
Tuesday, February 14, 2006
Baby Hack
 Todd Vanderlin documents an experiment: "I bought a $10 electronic baby in china town. I cracked it open and soldered a couple of switches to the the speaker. Now the baby is possessed and I have hacked a baby." Don't miss the video here.
Todd Vanderlin documents an experiment: "I bought a $10 electronic baby in china town. I cracked it open and soldered a couple of switches to the the speaker. Now the baby is possessed and I have hacked a baby." Don't miss the video here.
Monday, February 13, 2006
Nmap 4.01 Released!
You can find 4.01 at the normal location:
http://www.insecure.org/nmap/download.html
Sunday, February 12, 2006
Saturday, February 11, 2006
Secure Travel - Head Found in Luggage
 If you are going to carry a spare head, make sure you declare it at customs!
If you are going to carry a spare head, make sure you declare it at customs!US immigration officials have arrested a Haitian woman after baggage screeners found a human head in her luggage at a Florida airport.
Myrlene Severe, 30, has been charged with failing to declare the head on a customs form and transporting "hazardous material".
A spokesman for Miami's immigration and customs agency told the AFP news agency that the head was not simply a skull.
"It had teeth, hair and skin, and quite a lot of dirt," she said.
Privacy Watchdog: Beware Google Desktop
The new feature, dubbed "Search Across Computers," caches users' text contents--including PDFs, spreadsheets, Word documents, e-mails, and other documents--on Google's servers, so that users can search them from any computer with an Internet connection. The EFF, however, claims that the feature puts users' data at risk. "EFF urges consumers not to use this feature, because it will make their personal data more vulnerable to subpoenas from the government and possibly private litigants, while providing a convenient one-stop-shop for hackers who've obtained a user's Google password," the foundation said in a statement.
Friday, February 10, 2006
Friday Fun - Burglar Checks email
Lori Menzel of the town of Kewaskum said the burglar left his Yahoo account open after checking his personal e-mail on the computer at her home.
``He never logged out,'' she said, adding: ``He made himself at home here. He spent some time in our bedroom trying on my husband's clothes. I could tell he went through some of my clothes.''
John the Ripper 1.7 Release is out
* Bitslice DES code for x86 with MMX: more than twice faster than older non-bitslice MMX code.
* Bitsliced the LM hash code as well: now several times faster.
* Significant improvements to the generic bitslice DES code: +20% on RISC.
* PowerPC G4+ AltiVec support (Mac OS X and Linux): effective 128-bitness for bitslice DES, resulting in huge speedups.
* First attempt at generic vectorization support for bitslice DES.
* Two MD5 hashes at a time for extra ILP on RISC: up to +80% on Alpha EV5+.
* Generic Blowfish x86 assembly code in addition to the original Pentium version: +15% on the Pentium Pro family (up to and including Pentium III), +20% on AMD K6 (Pentium 4 and newer AMD CPUs are more happy running the original Pentium code for Blowfish).
* Verbose logging of events to the global or a session-specific log file.
* Better idle priority emulation with POSIX.1b (POSIX.4) scheduling calls.
* System-wide installation support for *BSD ports and Linux distributions.
* AIX, DU/Tru64 C2, HP-UX tcb files support in unshadow.
* New make targets for Linux/x86-64, Linux/PowerPC, FreeBSD/Alpha, OpenBSD/x86-64, OpenBSD/Alpha, OpenBSD/SPARC, OpenBSD/SPARC64, OpenBSD/PowerPC, OpenBSD/PA-RISC, OpenBSD/VAX, NetBSD/VAX, Solaris/SPARC64, Mac OS X (PowerPC and x86), SCO, BeOS.
* Bug and portability fixes, and new bugs.
* Bonus: "Strip" cracker included in the default john.conf (john.ini).
Thursday, February 09, 2006
Police Beat
Ark. Police Chief, His Wife, Mayor Arrested
It's a lot for an Arkansas town of fewer than 4,300 residents to stomach in one day.
Florida Deputy Uses Car-cam to Tape Women
A sheriff's deputy in Martin County is accused of dishonoring his badge after he was caught videotaping scantily clad women while he was on patrol.
Wednesday, February 08, 2006
A Day in The Life of Chinese Internet Police
Pen Test Live CD 'Arudius' Reaches v0.5
 One more tool to play with...
One more tool to play with...This release features the addition of some novel security tools - tools for passive network discovery by analyzing broadcast traffic, very fast SMB password cracking tool and a UPnP device discovery tool analyzing M-SEARCH packets, to mention a few among others.
You can find it here.
Black Hat Fingers Email As Easy Target
Admins who allow email clients to receive unadulterated HTML documents are opening a hole in network security that can be very difficult to defend... especially once an attacker is inside the network perimeter.
HTML makes it easy to duplicate the appearance of groups from whom the end user regularly receives HTML messages, like banks, credit card companies and online auction houses. And hiding links to phishing or malware sites beneath apparently legitimate URLs is elementary.
When you add the potential havoc caused by attachments, ActiveX, Java, VBscript, and javascript... well, you get the picture. You open the door to all manner of rootkit, backdoor, keylogger, etc.
Sleeper Bugs used to Steal 1million in France
Police say the virus is embedded in emails or websites and remains dormant until the user contacts their bank online. When that happens, the bug becomes active and records passwords and bank codes which are then forwarded to the thieves. They then use the information to check the victim has money in the bank before transferring funds to the accounts of third parties, known as mules, who may have agreed to allow money to pass through their accounts in return for a commission of between 5% and 10%.
Police claim this is set up through fictitious companies, including one American firm named World Transfer, although the mules could be unaware that their computers are being used for theft.
Tuesday, February 07, 2006
BOA Allows ID Theft to Continue
 Margaret Harrison, a young wife and mother living in San Diego, first noticed the problem four years ago when she applied for unemployment.
Margaret Harrison, a young wife and mother living in San Diego, first noticed the problem four years ago when she applied for unemployment.“They asked if I worked on a horse ranch in eastern Washington, and I said no,” laughs Harrison. “[I’m] not quite the rancher type.”
She investigated and found out a laborer named Pablo has been using her Social Security number. And while Margaret pays for credit monitoring, she says the Equifax credit reporting bureau never noticed the problem until she told the agency. Now Equifax has put a fraud alert on her account. And then there’s this: Last month, the Bank of America sent her a new debit card bearing her name and Pablo’s picture!
Margaret says the Bank of America claims it can’t take any action against Pablo because he pays his bills on time — that her case is in what they call “a reactive state.”
“Because currently it’s not negatively impacting my credit, so I have no legal recourse for any action,” says Harrison.
Customer Service?
The Topology of Covert Conflict
Interesting research paper by Shishir Nagaraja and Ross Anderson. Implications for warfare, terrorism, and peer-to-peer file sharing:
Abstract:Often an attacker tries to disconnect a network by destroying nodes or edges, while the defender counters using various resilience mechanisms. Examples include a music industry body attempting to close down a peer-to-peer file-sharing network; medics attempting to halt the spread of an infectious disease by selective vaccination; and a police agency trying to decapitate a terrorist organisation. Albert, Jeong and Barabási famously analysed the static case, and showed that vertex-order attacks are effective against scale-free networks. We extend this work to the dynamic case by developing a framework based on evolutionary game theory to explore the interaction of attack and defence strategies. We show, first, that naive defences don’t work against vertex-order attack; second, that defences based on simple redundancy don’t work much better, but that defences based on cliques work well; third, that attacks based on centrality work better against clique defences than vertex-order attacks do; and fourth, that defences based on complex strategies such as delegation plus clique resist centrality attacks better than simple clique defences. Our models thus build a bridge between network analysis and evolutionary game theory, and provide a framework for analysing defence and attack in networks where topology matters. They suggest definitions of efficiency of attack and defence, and may even explain the evolution of insurgent organisations from networks of cells to a more virtual leadership that facilitates operations rather than directing them. Finally, we draw some conclusions and present possible directions for future research.
Sunday, February 05, 2006
BackTrack beta Released Today!
 Distribution Info:
Distribution Info:BackTrack is released in two flavours - Developer Edition and User Edition. These two CD's contain the same data, however have the following differences:Developer Edition
* Built from the individual modules which create BackTrack.
* Boot time is slow, due to large number of modules.
* Modulatiry is high, so user customisation is easier.
User Edition
* Individual modules consolidated.
* Boot time is faster, due to few modules.
* Modulatiry is low, so user customisation is harder.
You can download it here.
UK ID Fraud Figures 'inflated to play on public fears'
In a report published yesterday, the Home Office said that the annual cost of ID fraud had reached £1.7 billion. However, this figure was undermined by Apacs, the group that represents payment organisations such as banks and credit firms, which said that the cost had been grossly overestimated and that its own figures had been misrepresented.
Asked why the Home Office used the larger sum, she said: “I just think they think it is a good story to scare people with.”
Superbowl Sunday
Friday, February 03, 2006
GPS-Enabled Dart
With that street-cop psychology, Chief William J. Bratton unveiled Thursday a new and decidedly strange weapon in the LAPD's effort to halt high-speed pursuits.
It is an air-propelled miniature dart equipped with a global positioning device. Once fired from a patrol car, it sticks to a fleeing motorist's vehicle and emits a radio signal to police.
Bratton hailed the dart as "the big new idea" and said that if the pilot program was successful, Los Angeles' seemingly daily TV fix of police chases could be a thing of the past.
"Instead of us pushing them doing 70 or 80 miles an hour … this device allows us not to have to pursue after the car," Bratton said. "It allows us to start vectoring where the car is. Even if they bail out of the car, we'll have pretty much instantaneously information where they are."
Fridays are for Fun - Karate Experts Hired to Control Parrots
 Organizers of a vintage car rally have hired karate experts to protect vehicles from marauding native parrots, a media report said Friday.
Organizers of a vintage car rally have hired karate experts to protect vehicles from marauding native parrots, a media report said Friday.Around 40 members of a local karate club have been enlisted to protect around 140 classic cars due to visit an alpine village near Mt. Cook on New Zealand's South Island on Sunday, the New Zealand Press Association reported.
The karate experts will protect the cars from Keas, sharp-beaked native parrots which have been known to damage vehicles in their search for shiny items, NZPA said.
Thursday, February 02, 2006
Embarrassing Messages From Enron's Email
A couple of swaths thru Andrew Fiore's searchable archive of Enron's email database is enough to remind us all that, no matter where you go or what you do, your email is forever...
Wednesday, February 01, 2006
Microsoft Officially Releases Internet Explorer 7 Beta 2 and Out Pops the first Advisory
Internet Explorer 7 Beta 2 Preview will only run on Windows® XP Service Pack 2 (SP2) systems, but will ultimately be available for Windows Vista, Windows XP Professional x64 Edition, and Windows Server 2003.
The Windows XP edition of IE 7 Beta 2 Preview can be downloaded from here.
And so it begins...
Advisory: sp-x23-advisorySo I saw that Microsoft released IE 7.0 Beta 2 to the public today. So, I figured I would give it a quick look at and I just happened to find something within the first 15 minutes into testing. Weird huh? So your probally thinking, why release an advisory on a beta product? Well, why not? Its Microsoft right? You can check out the advisory here, and the PoC here.. And for the ones not running windows, here is a screenshot if your interested...




