Friday, June 15, 2012
Thursday, April 26, 2012
Friday, April 13, 2012
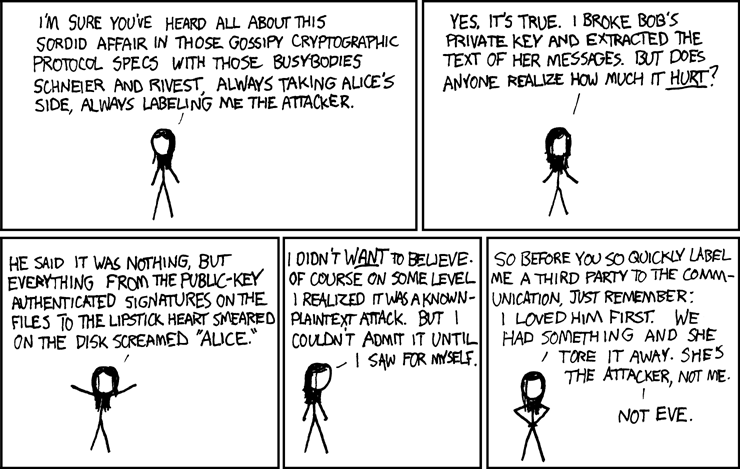
Who was the bigger boob?
Last week, Higinio O. Ochoa III was charged by the FBI with hacking into US law enforcement agencies and releasing phone numbers and home addresses of police officers. You're looking at the evidence the FBI used to nail him.
GIZMODO story here.
GIZMODO story here.
Labels:
Friday Fun
Monday, March 19, 2012
Friday, March 09, 2012
Tuesday, February 14, 2012
Friday, February 10, 2012
Tuesday, February 07, 2012
Benefits of being a CISSP
More good stuff here: http://www.youtube.com/user/InfosecCynic?feature=watch
Tuesday, December 13, 2011
Friday, December 09, 2011
Wednesday, November 30, 2011
Thursday, November 10, 2011
Wednesday, September 07, 2011
Friday, July 29, 2011
Wednesday, July 20, 2011
Saturday, July 16, 2011
Friday, July 01, 2011
Wednesday, June 22, 2011
Friday, March 18, 2011
Friday, February 18, 2011
Wednesday, January 26, 2011
Wednesday, December 08, 2010
Best SPAM Ever!
-----Original Message-----
From: Miss Freya [mailto:artzgale@gmail.com]
Sent: Wednesday, December 08, 2010 12:02 AM
To:
Subject: Dear Internet User
DEAR RECEIVER,
You have just received a Taliban virus. Since we are not so technologicaly advanced in Afghanistan, this is a MANUAL virus. Please delete all the files on your hard disk yourself and send this mail to everyone you know.
Thank you very much for helping us.
Thanks & Regard's
Miss Freya
From: Miss Freya [mailto:artzgale@gmail.com]
Sent: Wednesday, December 08, 2010 12:02 AM
To:
Subject: Dear Internet User
DEAR RECEIVER,
You have just received a Taliban virus. Since we are not so technologicaly advanced in Afghanistan, this is a MANUAL virus. Please delete all the files on your hard disk yourself and send this mail to everyone you know.
Thank you very much for helping us.
Thanks & Regard's
Miss Freya
Sunday, December 05, 2010
TWiT Live Specials 52: Tron: Legacy
TWiT Live Specials 52: Tron: Legacy
Host: Sarah Lane
Behind the scenes of TRON: Legacy with the filmmakers and cast.
Host: Sarah Lane
Behind the scenes of TRON: Legacy with the filmmakers and cast.
Thursday, November 25, 2010
Wednesday, November 10, 2010
Saturday, October 16, 2010
Saturday, September 25, 2010
Practical Lock Picking: A Physical Penetration Tester's Training Guide [Paperback]
Great book for the beginner or an old pro. Been reading lock picking books for 35 years and this is one of the best... Deviant Ollam, one of the security industry's best-known lockpicking teachers, has assembled an instructional manual geared specifically toward penetration testers. Unlike other texts on the subject (which tend to be either massive volumes detailing every conceivable style of lock or brief "spy manuals" that only skim the surface) this book is for INFOSEC professionals that need essential, core knowledge of lockpicking and seek the ability to open most locks with relative ease.
Friday, August 13, 2010
Sunday, August 01, 2010
Tuesday, July 27, 2010
Sunday, July 18, 2010
Cuban Spy Gets Life Without Parole, Wife Gets 6 ½ Years
The 73-year-old great grandson of Alexander Graham Bell was sentenced Friday to life in prison without parole for quietly spying for Cuba for nearly a third of a century from inside the State Department. His wife was sentenced to 5½ years.
Retired intelligence analyst Kendall Myers said he meant his country no harm and stole secrets only to help Cuba's people who "have good reason to feel threatened" by U.S. intentions of ousting the communist Castro government.
But U.S. District Judge Reggie Walton said Myers and his 72-year-old wife, Gwendolyn, had betrayed America and should receive heavy punishment.
Full background story here.
Retired intelligence analyst Kendall Myers said he meant his country no harm and stole secrets only to help Cuba's people who "have good reason to feel threatened" by U.S. intentions of ousting the communist Castro government.
But U.S. District Judge Reggie Walton said Myers and his 72-year-old wife, Gwendolyn, had betrayed America and should receive heavy punishment.
Full background story here.
Labels:
Spy
Friday, July 16, 2010
Wednesday, July 14, 2010
Friday, July 09, 2010
Saturday, June 26, 2010
Friday, June 11, 2010
Wednesday, May 12, 2010
Sunday, May 02, 2010
Mine is due to arrive tomorrow, more soon...
本: běn. The Chinese character 本 signifies an origin or the beginning place; It signifies exactly what the first version of the NanoNote is: a beginning.
The 本 version of NanoNote is an ultra small form factor computing device. The device sports a 336 MHz processor, 2GB of flash memory, microSD slot, head phone jack, USB device and 850mAh Li-ion battery. It boots Linux out of the box and also boots over USB. It’s targeted squarely at developers who see the promise of open hardware and want to roll their own end user experience. It’s the perfect companion for open content; we envision developers turning the device into a music or video player for Ogg or an offline Wikipedia or MIT OpenCourseWare appliance. Or you can simply amaze your friends by creating an ultra small handheld notebook computer. You choose the distribution. The 本 Nanonote is the first in a line of products that will see the addition of other hardware capabilities. Get your NanoNote and start a Nanoproject today. Or join one of the existing projects in our developer community.
本: běn. The Chinese character 本 signifies an origin or the beginning place; It signifies exactly what the first version of the NanoNote is: a beginning.
The 本 version of NanoNote is an ultra small form factor computing device. The device sports a 336 MHz processor, 2GB of flash memory, microSD slot, head phone jack, USB device and 850mAh Li-ion battery. It boots Linux out of the box and also boots over USB. It’s targeted squarely at developers who see the promise of open hardware and want to roll their own end user experience. It’s the perfect companion for open content; we envision developers turning the device into a music or video player for Ogg or an offline Wikipedia or MIT OpenCourseWare appliance. Or you can simply amaze your friends by creating an ultra small handheld notebook computer. You choose the distribution. The 本 Nanonote is the first in a line of products that will see the addition of other hardware capabilities. Get your NanoNote and start a Nanoproject today. Or join one of the existing projects in our developer community.
Friday, March 26, 2010
Monday, March 15, 2010
Salmonella outbreak tracked by shopper cards
What do you think - good thing or bad? Can certainly see the good use, but what if used for the wrong reasons? A witch hunt of sorts...
Health authorities in the U.S. have for the first time used department store credit cards to help trace the source of a recent salmonella outbreak that left hundreds of Americans ill.
Investigators at the Centers for Disease Control and Prevention were scrambling to find the source of the outbreak when they hit upon the idea of tracking grocery purchases of those who became ill.
With permission from the patients, health authorities followed the trail of grocery purchases to a Rhode Island company that makes salami, then zeroed in on the pepper used to season the meat.
Read more: http://www.cbc.ca/health/story/2010/03/12/consumer-salmonella.html#ixzz0iFhw2XUI
Health authorities in the U.S. have for the first time used department store credit cards to help trace the source of a recent salmonella outbreak that left hundreds of Americans ill.
Investigators at the Centers for Disease Control and Prevention were scrambling to find the source of the outbreak when they hit upon the idea of tracking grocery purchases of those who became ill.
With permission from the patients, health authorities followed the trail of grocery purchases to a Rhode Island company that makes salami, then zeroed in on the pepper used to season the meat.
Read more: http://www.cbc.ca/health/story/2010/03/12/consumer-salmonella.html#ixzz0iFhw2XUI
Saturday, March 13, 2010
Friday, March 12, 2010
Thursday, March 11, 2010
Rainbow Tables hosted on an SSD
New work on a rainbow table system that will crack a 14 char XP password in
under 6 seconds.
Read about it here.
Try it out: demo
under 6 seconds.
Read about it here.
Try it out: demo
SANS/CWE Top 25 Dangerous Programming Errors list
SANS/CWE released a top 25 dangerous programming errors list. It contains their list of the most common errors that developers are likely to make. The intention is to raise awareness to these problems and help prioritize the order of importance for organizations new into the security game. Their blog has been covering each of the Top 25 problems and provides some commentary on each of them. They are up to #13
Read all about it here.
Read all about it here.
Wednesday, March 10, 2010
Friday, March 05, 2010
Wednesday, March 03, 2010
Report: The Command Structure of the Aurora Botnet: History, Patterns, and Findings
Did the "experts" get it wrong? Were the attacks on Google by amateurs?
"Many security vendors have explained the operation against Google, dubbed “Operation Aurora,” using a military vernacular. However, based upon analysis of exhaustive data surrounding these attacks and examination of both the malware and the CnC topologies used by the criminals behind Aurora, it appears that this threat can best be classified as a just another common botnet attack – and one that is more amateur than average."
Read the report from Damballa here.
"Many security vendors have explained the operation against Google, dubbed “Operation Aurora,” using a military vernacular. However, based upon analysis of exhaustive data surrounding these attacks and examination of both the malware and the CnC topologies used by the criminals behind Aurora, it appears that this threat can best be classified as a just another common botnet attack – and one that is more amateur than average."
Read the report from Damballa here.
Monday, March 01, 2010
Defrauding and Hacking Ticketmaster
This really a hack?
"To defeat the Online Ticket Vendors' technologies, the defendants worked with computer programmers in Bulgaria to establish a nationwide network of computers that impersonated individual visitors to the Online Ticket Vendors' websites, the indictment alleges. The network – described as the "CAPTCHA Bots" in the indictment – gave Wiseguys the ability to flood the Online Ticket Vendors' computers at the exact moment that event tickets went on sale."
Full story here.
"To defeat the Online Ticket Vendors' technologies, the defendants worked with computer programmers in Bulgaria to establish a nationwide network of computers that impersonated individual visitors to the Online Ticket Vendors' websites, the indictment alleges. The network – described as the "CAPTCHA Bots" in the indictment – gave Wiseguys the ability to flood the Online Ticket Vendors' computers at the exact moment that event tickets went on sale."
Full story here.
Friday, February 26, 2010
UBS Access Key (IBM Zone Trusted Information Channel)
What do you think... good idea? Biz banking saver?
Wednesday, February 24, 2010
Friday, February 19, 2010
Wednesday, February 17, 2010
Martial Law for Cyberspace?
Danger Will Robinson - the iPhone will be the end of civilization!
The federal government isn't prepared to cope with a widespread cyber attack, former top Bush and Clinton administration officials said Tuesday.
The officials participated in a public cybersecurity war game, where they simulated how the government would respond to a widespread cyber attack. The scenario started with malware spread through an iPhone app; the attack eventually crippled cell phone networks and Internet service, and it ended with much of the East Coast without power due to a failing electrical grid.
Full story here.
The federal government isn't prepared to cope with a widespread cyber attack, former top Bush and Clinton administration officials said Tuesday.
The officials participated in a public cybersecurity war game, where they simulated how the government would respond to a widespread cyber attack. The scenario started with malware spread through an iPhone app; the attack eventually crippled cell phone networks and Internet service, and it ended with much of the East Coast without power due to a failing electrical grid.
Full story here.
Simon the IT Dummy
This whole series rocks. Simon the IT Dummy, the poster boy for under appreciated IT (Security) people everywhere.
Tuesday, February 16, 2010
Sunday, February 14, 2010
Cloud security news and whimsy sans the bullshit.
Similar format to Liquidmatrix.org a new site dedicated to cloud security.
Tuesday, February 09, 2010
Wednesday, January 27, 2010
How to catch an iPhone thief
Thanks to Brian Krebs for finding... this is a way cool story.
Monday - The Setup
The rest of the story here.
Monday - The Setup
The whole thing started when my plane landed in Los Angeles on Monday afternoon at 2:55pm coming from Cabo San Lucas. The guy sitting next to me on the plane asked me to loan him a pen so that he could fill out his customs form. I watched him fill out the form and clearly remember his birth year of 1984, but am a bit unsure about his name. I think it was -----, but in this story, we will refer to him as Pinche.
The rest of the story here.
Wednesday, January 20, 2010
Sunday, January 17, 2010
Friday, January 15, 2010
Note to terrorist
You really want to terrorize the US? Just put a dud bomb in your butt, get on a plane and tell people about it. Next up... cavity searches for everyone!
Labels:
Friday Fun
Thursday, January 14, 2010
Robertson: Haiti had pact with devil
WTF! Why not blame it on the Easter Bunny or Santa. Relating what he called a "true story," Rev. Pat Robertson asserted on his TV show, "The 700 Club" that Haiti was struck by a devastating earthquake because its founding fathers made a pact with the devil.
Wednesday, January 13, 2010
Monday, January 11, 2010
Thursday, January 07, 2010
Fun site for toys
Some of the product descriptions are a fun read...
http://www.chinawholesale365.com/
http://www.chinawholesale365.com/
Labels:
Friday Fun
Wednesday, December 30, 2009
The Coolest Data Center Video Tours
Here’s a look at five of the coolest video tours of major data centers, along with a list of links to 10 other worthwhile video tours.
Saturday, December 26, 2009
Thursday, December 24, 2009
Friday, November 27, 2009
Some Interesting Password Data from MS
Do and don’ts for p@$$w0rd$
Full story here.
Here is a top 10 list with the most common user names used in automated attacks:
| User names | Count |
| Administrator | 136971 |
| Administrateur | 107670 |
| admin | 8043 |
| andrew | 5570 |
| dave | 4569 |
| steve | 4569 |
| tsinternetuser | 4566 |
| tsinternetusers | 4566 |
| paul | 4276 |
| adam | 3287 |
And a similar list for passwords:
| Passwords | Count |
| password | 1188 |
| 123456 | 1137 |
| #!comment: | 248 |
| changeme | 172 |
| F**kyou (edited) | 170 |
| abc123 | 155 |
| peter | 154 |
| Michael | 152 |
| andrew | 151 |
| matthew | 151 |
Full story here.
Tuesday, November 24, 2009
Thursday, November 19, 2009
Monday, November 09, 2009
Sunday, November 08, 2009
Job Security
Every year, Americans eat 35 million cows, 115 million pigs, and 9 billion chickens and turkeys.
- The New Yorker
- The New Yorker
Monday, October 26, 2009
Saturday, October 24, 2009
Friday, October 16, 2009
Social engineering for penetration testers
Sharon Conheady's BruCON talk discusses the practical aspects of a social engineering attack, providing plenty of war stories from her career as a social engineer. The key to preventing social engineering attacks from being successful lies in education and awareness. This talk will give the audience an insight into the techniques used by social engineers, whether as part of an ethical social engineering test or as a malicious social engineering attack.
Social engineering for penetration testers - Sharon Conheady - BruCON 2009 from security4all on Vimeo.
Thursday, October 15, 2009
30 years of Failure: the Username/Password combo.
Interesting new study, which is being published by the Human Factors and Ergonomics Society.
"The use of alphanumeric usernames and passwords is the
most often used (and also the cheapest) method of computer
authentication. However, unfortunately human beings are
limited in their information processing capabilities (Cowan, et
al., 2008). People either use simple passwords that are easy to
remember but easy to crack or difficult passwords which are
difficult to remember. Results of our study have shown that
there are very few people who do not deviate from the best
practices for password use."
"The use of alphanumeric usernames and passwords is the
most often used (and also the cheapest) method of computer
authentication. However, unfortunately human beings are
limited in their information processing capabilities (Cowan, et
al., 2008). People either use simple passwords that are easy to
remember but easy to crack or difficult passwords which are
difficult to remember. Results of our study have shown that
there are very few people who do not deviate from the best
practices for password use."
Saturday, October 10, 2009
CNN Money - 50 Best Jobs in America
8. Computer/Network Security Consultant
Median salary (experienced): $99,700
Top pay: $152,000
Job growth (10-year forecast): 27%
Sector: Information Technology
What they do: Protect computer systems and networks against hackers, spyware, and viruses. "I consider myself a cybercrime fighter," says Gregory Evans, an independent computer security consultant in Atlanta.
Why it's great: No company or government agency can afford to have a serious breach in the security of its computer system. New technologies and an unending supply of creative hackers around the world keep the field challenging. Consultants can often work from home. And top-level pros command big paychecks.
Drawbacks: Talk about stress. If a system is infiltrated by a virus or hacker, it could mean lights out for the security consultant's career. "This is a job you can't afford to ever fail in," says Evans.
Pre-reqs: Mostly major geekdom, since the skills can be self-taught. Still, a computer science degree comes in handy. An information systems security professional certification (CISSP) is increasingly favored. Experience is key for better-paying positions: Most companies won't hire a consultant with less than five years of experience.
Story here.
Median salary (experienced): $99,700
Top pay: $152,000
Job growth (10-year forecast): 27%
Sector: Information Technology
What they do: Protect computer systems and networks against hackers, spyware, and viruses. "I consider myself a cybercrime fighter," says Gregory Evans, an independent computer security consultant in Atlanta.
Why it's great: No company or government agency can afford to have a serious breach in the security of its computer system. New technologies and an unending supply of creative hackers around the world keep the field challenging. Consultants can often work from home. And top-level pros command big paychecks.
Drawbacks: Talk about stress. If a system is infiltrated by a virus or hacker, it could mean lights out for the security consultant's career. "This is a job you can't afford to ever fail in," says Evans.
Pre-reqs: Mostly major geekdom, since the skills can be self-taught. Still, a computer science degree comes in handy. An information systems security professional certification (CISSP) is increasingly favored. Experience is key for better-paying positions: Most companies won't hire a consultant with less than five years of experience.
Story here.
Friday, October 09, 2009
Happy Meal?
Someone dressed an already dead deer in a clown outfit and wig, and dropped it for a family to see.
Labels:
Friday Fun
Saturday, October 03, 2009
Banking Trojan Infections Tripled.
Banking trojan infections almost tripled (up 186 per cent) between Q4 2008 and Q2 2009 according to APWG report.
Wednesday, September 30, 2009
Crooks, Trojans & Mules
Interesting report from finjan.
In the third issue of its Cybercrime Intelligence Report for 2009, Finjan shows how cybercrooks used a combination of Trojans and money mules to rake in hundreds of thousands of Euros and to minimize detection by the anti-fraud systems used by banks. After infection, a bank Trojan was installed on the victims’ machines and started communication with its Command & Control (C&C) server for instructions. These instructions included the amount to be stolen from specific bank accounts and to which money mule-accounts the stolen money should be transferred. The use of this Anti anti-fraud method signals a new trend in cybercrime.
Saturday, September 26, 2009
OWASP Podcast Series #41
David Rice, is an internationally recognized information security professional and an accomplished educator and visionary. For a decade he has advised, counseled, and defended global IT networks for government and private industry. David has been awarded by the U.S. Department of Defense for “significant contributions” advancing security of critical national infrastructure and global networks. Additionally, David has authored numerous IT security courses and publications, teaches for the prestigious SANS Institute, and has served as adjunct faculty at James Madison University. He is a frequent speaker at information security conferences and currently Director of The Monterey Group.
Listen
Listen
Friday, September 25, 2009
A Stick Figure Guide to the Advanced Encryption Standard (AES)
A very nice explanation of AES, even has example code with it...
Man sues BofA for "1,784 billion, trillion dollars"
More Friday Fun!
Dalton Chiscolm is unhappy about Bank of America's customer service -- really, really unhappy.
Dalton Chiscolm is unhappy about Bank of America's customer service -- really, really unhappy.
Chiscolm in August sued the largest U.S. bank and its board, demanding that "1,784 billion, trillion dollars" be deposited into his account the next day. He also demanded an additional $200,164,000, court papers show.
Reuters story here.
Labels:
Friday Fun
Thursday, September 24, 2009
Couple's Lawsuit Against Bank Over Breach To Move Forward
So who is responsible the Bank/FI or the end user?
A U.S. District Court ruling in a lawsuit against a bank over a hacked online account has raised thorny questions about who's ultimately responsible for the breach of a customer's account.
An Illinois district court denied Citizens Financial Bank's request to dismiss a lawsuit that charges the bank was negligent in protecting a couple's bank account after their user name and password were stolen and used to pilfer $26,000 from their account. The ruling lets the couple, Marsha and Michael Shames-Yeakel, continue with their lawsuit, mostly based on their allegations that the bank failed to properly secure their account.
Full story here.
A U.S. District Court ruling in a lawsuit against a bank over a hacked online account has raised thorny questions about who's ultimately responsible for the breach of a customer's account.
An Illinois district court denied Citizens Financial Bank's request to dismiss a lawsuit that charges the bank was negligent in protecting a couple's bank account after their user name and password were stolen and used to pilfer $26,000 from their account. The ruling lets the couple, Marsha and Michael Shames-Yeakel, continue with their lawsuit, mostly based on their allegations that the bank failed to properly secure their account.
Full story here.
Tuesday, September 22, 2009
Monday, September 21, 2009
ShmooCon 2010 - Registration
Important Dates and Deadlines
* November 1, 2009, Noon EDT - first round of ticket sales
* December 1, 2009, Noon EST - second round of ticket sales
* January 1, 2010, Noon EST - third and final round of ticket sales
* November 1, 2009, Noon EDT - first round of ticket sales
* December 1, 2009, Noon EST - second round of ticket sales
* January 1, 2010, Noon EST - third and final round of ticket sales
Labels:
ShmooCon
Monday, September 14, 2009
Don't Copy That 2 (Official Sequel to Don't Copy That Floppy)
In this sequel to 1992's "Don't Copy That Floppy," MC Double Def DP continues his crusade against piracy in the digital age. Brought to you by SIIA (formerly SPA).
What do you think?
What do you think?
Thursday, September 10, 2009
Cyber War Gets Its Own Museum Show
The International Spy Museum in Washington plans will launch a cyber war show dubbed Weapons of Mass Disruption next month.
The show will be heavy on video interviews with folks such as Director of National Intelligence Dennis Blair; former Special Advisor to the President on Cyber Security Richard A. Clarke; Lee Hamilton, co-author of The 9/11 Commission Report; Sen. Christopher "Kit" Bond, vice chairman of the Senate Select Committee on Intelligence; and R. James Woolsey, former CIA director.
The show will be heavy on video interviews with folks such as Director of National Intelligence Dennis Blair; former Special Advisor to the President on Cyber Security Richard A. Clarke; Lee Hamilton, co-author of The 9/11 Commission Report; Sen. Christopher "Kit" Bond, vice chairman of the Senate Select Committee on Intelligence; and R. James Woolsey, former CIA director.
Story here.
Spy Museum
Tuesday, September 08, 2009
Vista/2008/Windows 7 SMB2 BSD 0Day
Is this not a one big "Well Duh"?
If you are not blocking 445 then... you have more problems than this one...
From SANS -
"We have received a report from Tyler that a vulnerability affecting Microsoft SMB2 can be remotely crashed with proof-of-concept code that has been published yesterday and a Metasploit module is out.
We have confirmed it affects Windows 7/Vista/Server 2008. The exploit needs no authentication, only file sharing enabled with one 1 packet to create a BSOD. We recommend filtering access to port TCP 445 with a firewall.
Windows 2000/XP are NOT affected by this exploit."
If you are not blocking 445 then... you have more problems than this one...
From SANS -
"We have received a report from Tyler that a vulnerability affecting Microsoft SMB2 can be remotely crashed with proof-of-concept code that has been published yesterday and a Metasploit module is out.
We have confirmed it affects Windows 7/Vista/Server 2008. The exploit needs no authentication, only file sharing enabled with one 1 packet to create a BSOD. We recommend filtering access to port TCP 445 with a firewall.
Windows 2000/XP are NOT affected by this exploit."
Monday, September 07, 2009
Friday, September 04, 2009
Have Skimmer, will Travel

Police in New Zealand have apprehended two Bulgarian nationals in Nelson overnight. The Bulgarians have been charged with carrying out data-skimming attacks on ATM machines in Nelson and Canterbury, the NZPA has reported on September 4. Reportedly, the police investigation is still ongoing, with authorities trying to determine whether the pair were successful in their scheme, and if so, to assess the damages.
More here.
Wednesday, September 02, 2009
Weaponizing the Web from DEFCON
Shawn Moyer and Nathan Hamiel spent some time last year looking at this problem as it related specifically to social networks. This year, they talk about a previously unnoticed attack vector for lots and lots of web applications with user-generated content, and releasing a handy tool to exploit it.
Shawn Moyer and Nathan Hamiel: Weaponizing the Web (DefCon 17) from Vim EeeeOOO on Vimeo.
Happy Birthday INET
September 2, 1969, ARPANET, the forerunner of INTERNET was developed when two computers at University of California, Los Angeles were connected on an experimental military network by a team at UCLA.
Wikipedia ARPANET Timeline
Wikipedia ARPANET Timeline