From F-Secure Blog...
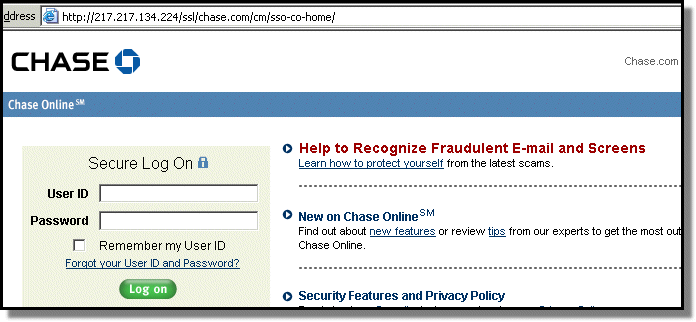
This phishing site is running on an infected home computer in Spain. Only the html is hosted there; all the images are actually loaded directly from a real chase.com server.
Now, activity like this could be detected by the website of the bank automatically. How about modifying the logic of the bank web server to do something along these lines:
If somebody
a) loads my images but
b) does not load the corresponding html file and
c) has http referrer -values outside of my domain
then, for this user, lets change this image:
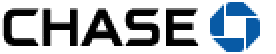
to this image:

This could be activated only after the activity has happened from, say, 10 different IP addresses, to make it harder for the attackers to spot it until it's too late.
And, in most cases the REFERRER fields would directly point the bank staff to the real phishing site which they could now start closing down.
Eventually, attackers would move to host their own images, but for now they still typically don't.
 In Waldo, people have held prayer vigils and protests aimed at an adult bookstore along US 301, trying to keep the "Cafe Risque" from opening its doors on time.
In Waldo, people have held prayer vigils and protests aimed at an adult bookstore along US 301, trying to keep the "Cafe Risque" from opening its doors on time.