Saturday, September 09, 2006
Monday, September 04, 2006
Saturday, September 02, 2006
The "Janus Project"
 The "Janus Project" is the brainchild of Kyle Williams of the Janus Wireless Security Research Group in Portland, Oregon.
The "Janus Project" is the brainchild of Kyle Williams of the Janus Wireless Security Research Group in Portland, Oregon.Mounted inside an epoxy and silicone-sealed watertight case lives a 1.5GHz C7 powered EPIA EN 15000G motherboard, 2 x four-port PCI to mini-PCI adapters, 8 x 802.11a/b/g mini-PCI WLAN Modules, 2 x 1W 2.4Ghz WLAN amplifiers, a keyboard and a 17in LCD screen. The system can scan up to 300 wireless networks simultaneously, storing and AES encrypting in real time all the data onto its 20GB hard drive.

By focusing all 8 WLAN cards onto an access point and using a combination of common Linux tools, the Janus Project can crack a WEP key in under 5 minutes. WPA and WPA2 encryption aren't far behind - Kyle and his friend Martin Peck are optimising the software to use the Padlock hardware acceleration of the C7 chip to crack those too.
If Kyle gets captured in enemy territory and tortured, an "Instant Off" switch will render the captured data useless until a password is entered and a USB stick containing a 2000-bit passkey is inserted. Presumably during the torturing process.
Friday, September 01, 2006
Friday Fun - Burning Man 2006 TV
 Burning Man 2006 is now in full swing and Current TV has setup an online television station, TV Free Burning Man.
Burning Man 2006 is now in full swing and Current TV has setup an online television station, TV Free Burning Man.They have been shooting video, doing interviews and uploading a daily show from Black Rock City. They will be doing a live broadcast the burn on Saturday night (September 2nd) starting at 9 PM PST/12 AM EST.
Thursday, August 31, 2006
Turning IE into a private Adult Content Browser
PI announces the 2006 Stupid Security Competition
Privacy International is calling for nominations to name and shame the worst offenders. The competition closes on October 31st 2006. The award categories are:
- Most Egregiously Stupid Award
- Most Inexplicably Stupid Award
- Most Annoyingly Stupid Award
- Most Flagrantly Intrusive Award
- Most Stupidly Counter Productive Award
The competition will be judged by an international panel of well-known security experts, public policy specialists, privacy advocates and journalists.
The competition is open to anyone from any country. Nominations can be sent to stupidsecurity@privacy.org.
Details of previous award winners can be found below, or at http://www.privacyinternational.org/ssa2003winners.
WIFI Camera Prototype
 Nice use for the cans from a favorite snack...
Nice use for the cans from a favorite snack...Wednesday, August 23, 2006
Blackjacking - 0wning the Enterprise via the Blackberry
Abstract:
This presentation will demonstrate how an attacker could utilize many typical corporate blackberry deployments to directly attack machines on the internal network—behind your perimiter defenses! The tools and source code presented will be available for attendees. Techniques for reducing the risks associated with this technology will also be presented.
Materials:
| Presentation Slides | Blackberry Attack Toolkit (Including BBProxy) |
Tuesday, August 22, 2006
Privacy Debacle Hall of Fame
10. ChoicePoint data spill
9. VA laptop theft
8. CardSystems hacked
7. Discovery of data on used hard drives for sale
6. Philip Agee's revenge
5. Amy Boyer's murder
4. Testing CAPPS II
3. COINTELPRO
2. AT&T lets the NSA listen to all phone calls
1. The creation of the Social Security Number
Friday, August 18, 2006
Blackhat 06 Presentations
Cool speed test site
Wireless networking source - .\\etrix Communication LLC
 Interesting source for wireless networking software, parts, supplies and info.
Interesting source for wireless networking software, parts, supplies and info.
Fridays are for fun! Secret Agent Earphones
 Easy way to make FBI-escque earphones. This is very useful if you ever want to listen to music but also have one ear free (for instance while biking in the city)
Easy way to make FBI-escque earphones. This is very useful if you ever want to listen to music but also have one ear free (for instance while biking in the city)
Sunday, August 06, 2006
Mystery hole opens in Cisco firewall
A security researcher has demonstrated how an unpatched vulnerability in Cisco?s PIX firewall appliances could allow outside attackers to gain access to corporate networks. On the final slide of his presentation at the Black Hat show on VoIP security, Hendrik Scholz, a developer with Freenet Cityline disclosed a technique for bypassing the firewalls, according to an audio recording of the talk obtained by IDG News. "You can open up whatever port you want... and access internal servers from the outside," he said "It's really easy to do and we're talking to Cisco about how to get it fixed." By now Black Hat is old hat for Cisco. Last year conference organisers were sued by the networking giant and had to literally rip a presentation by researcher Michael Lynn out of last year's conference materials because it disclosed flaws in its IOS software.
Phone numbers stations mystery revealed at DEFCON
Read the whole story here.
Friday, July 28, 2006
Hak5

Hak.5 is a video podcast for the hacker, modder and do-it-yourselfer. Hosted by Darren Kitchen and Wess Tobler on the 5th of each month, the show is a hybrid of technology and geek humor.
TOOOL, The Open Organisation of Lockpickers
 Weekend fun... Ck the blackbag blog for info from Hope # 6 and a look at the very nice Hope number six pickset...
Weekend fun... Ck the blackbag blog for info from Hope # 6 and a look at the very nice Hope number six pickset...
Dilbert - funny in a scary way...
 Tuesday's Dilbert (quoted below, copyright Scott Adams, Inc) funny in a scary way...
Tuesday's Dilbert (quoted below, copyright Scott Adams, Inc) funny in a scary way...Dilbert: Is it more important to follow our documented process or to meet the deadline? I only ask because our deadline is arbitrary and our documented process was pulled out of someone's lower torso.
PHB: Where's your artificial sense of urgency?
Dilbert: Teamwork killed it.
Cool and Illegal Wireless Hotspot Hacks
Wednesday, July 19, 2006
Shark Analyzer
For a complete list of changes, please refer to the 0.99.2 release notes. Official releases are available right now from the download page.
Tuesday, July 18, 2006
Phish Spoofs 2-Factor Authentication
 The first ever case of using a man-in-the-middle attack against an online bank was reported by the Post's Brian Krebs on Tuesday.
The first ever case of using a man-in-the-middle attack against an online bank was reported by the Post's Brian Krebs on Tuesday.The security industry has long predicted this type of man-in-the-middle attack; it was only a matter of time. The attack targeted Citibank's Citibusiness service and was designed to spoof the token key hardware device used by the bank's customers. The phishing site checked the logon credentials with the real site before rendering the results to the phishing victim. Enter an invalid password, and you got an invalid logon page. A man-in-the-middle attack checks everything done at the phishing site against the original, so everything should look and feel more genuine.
Exactly the same kind of attacks can be used to target other types of two-factor authentication, including one-time password sheets.
Saturday, July 15, 2006
Stevens' net neutrality expertise
In that light, this quote is sort of terrifying: "The internet is not something that you just dump something on. It's not a big truck. It's, it's a series of tubes.
Friday, July 14, 2006
VulnerabilityAssessment.co.uk
Friday Fun - Spy Gadgets
 "This is a collection of "spy equipment" we have found for sale around the internet. Everything here is completely real, is sold at online stores, and almost any item listed here costs less than $500, and often times can be bought for less than $200."
"This is a collection of "spy equipment" we have found for sale around the internet. Everything here is completely real, is sold at online stores, and almost any item listed here costs less than $500, and often times can be bought for less than $200."
Wednesday, July 12, 2006
Long Hacker Sentence Upheld
A federal appeals court upheld a nine-year prison term Monday for a hacker who tried and failed to steal customer credit-card numbers from the Lowe's chain of home improvement stores.
The Politics of Paranoia and Intimidation
Floyd Rudmin, a professor at a Norwegian university, uses the mathematics of conditional probability, known as Bayes' Theorem, to demonstrate that the NSA's surveillance cannot effectively detect terrorists unless both the percentage of terrorists in the population and the accuracy rate of their identification are far higher than they are.
Monday, July 10, 2006
Dictionary of Information Security (Paperback)
 Book Description
Book DescriptionFrom the Author
Their our lots of wurds in this book. Sum of the werds are big. They're are no pitchers in this book. If ewe like big wirds and no pitchers you will like this book.
The courier driver showed up at noon, today, with the box of author copies. So I can, with assurance (p. 13) state that the volume now actually exists in hardcopy. After four years of maintaining it mostly as a resource for those studying for the CISSP exam, it's now going to be available in bookstores for everyone.
It's been interesting, working with Syngress. Having worked with more traditional publishers, I was rather expecting the usual 2-3 months of contract negotiations, 2-3 months to get out the final manuscript (the book had, after all, already been basically finished: I'd been using it on the Website for some time), and the usual 4-6 months in copy editing and galley proofing. The contract negotiations took about a month and a half. I got the final contract May 18th. They wanted the manuscript on the 26th. I got the galley proofs on June 1st, and had them back to Syngress on June 4th. (Then there seems to have been some kind of hiccup with the printer: it's been "due" every day now for about three weeks.)
So now, I suppose, I'd better get a move on. I've already replaced the glossary page (http://victoria.tc.ca/techrev/secgloss.htm) with an errata page, and I've got about 60 entries that need to be added or corrected. So I hope you'll all actually buy the book, and Syngress will be moved to putting out a new edition fairly soon. (And
regularly, after that.)
copyright Robert M. Slade, 2006 BKDCINSC.RVW 20060528
Sunday, July 09, 2006
Being a good brake - Security as a stress reducer
You’ve probably heard the analogy that security is like having brakes on an automobile. Brakes allow the driver to go faster, have more control and go where they want to go safely. While brakes are an inhibitor, they actually allow the driver to reach their destination in a safe, yet quick manner.
Imagine driving without them. You’d be a nervous wreck. (Okay, maybe not you, but most of us would be.) You’d go really slow; be afraid of changing directions; and feel stressed. Think: the only way to stop is to crash into something.In the paragraphs above, replace brakes with security (meaning security controls and processes) and driver with your organization’s name. Isn’t the concept the same? Security allows the user (driver) to reach their goal (destination) in a safe, yet quick manner. If you (security professionals) and your customers (users) are doing it right, security should allow the business to go faster, have control, and reach their goals safely without crashing.
The security team should be a stress reducer, not an inducer. Stress (in the negative connotation) comes when we feel out of control. Shouldn’t it be security’s job to introduce control and offer solutions for reducing risks and thereby reducing stress?
In recent years, the security group has gotten the bad reputation for being (a) a barrier to business, (b) an overhead without a quantifiable ROI, and (c) the hammer when there’s a breach or policy is not followed. In other words, they increased the stress for our organization. They weren’t being “good brakes.” This caused the organization to try to bypass security to get things done. (Don’t you try to avoid those things that cause you negative stress?)
Instead, we, the people in security need to be stress reducers. We need to be the brakes for our organization. However, there’s one difference: brakes are not normally seen, only felt; the security team needs to be both seen and felt. You do that by implementing proper controls and risk management processes.Security should collaborate with the business in identifying and assessing the risks and then implementing the proper controls to ensure the risk is appropriately mitigated for the business. (No more security for security sake.) This puts the business in control guided by security and reduces negative stress for everyone.
Security professionals: Next time you implementation a new technology, process or policy, ask yourself, “Am I being a ‘good brake’ or am I really adding negative stress?” You’d be surprised at how much better you will be received if you reduce your customer’s stress. Next week we’ll cover key steps you can take to become a security stress reducer.
By working together and helping each other, we all become stronger.
A Chronology of Data Breaches
Here's a chronology of data breaches since the ChoicePoint theft in February 2005.
Total identities stolen: 88,794,619.Should sensitive data be allowed to leave the nest at all, even if it is encrypted?
Why is so much private data allowed to be on laptops to begin with?
"It's pure laziness. There's actually no excuse for it," said Avivah Litan, a security analyst for Gartner Inc. "There's no good business reason for it."
If they absolutely need to analyze data out of the office, the employees should run programs that replace live credit card or Social Security numbers with random "dummy" figures whenever possible, since the actual numbers aren't always relevant.
Saturday, July 08, 2006
Coke case could spur review of security policies
In the Coke case, Joya Williams, 41, an administrative assistant who worked for the director of global brand marketing at Coca-Cola was the source of the trade secrets that were to be sold, prosecutors charged on Wednesday.
Not the safe, just the master key...Video surveillance showed Williams at her desk going through files in search of documents and stuffing them in her bags, prosecutors said.
While the episode highlights the importance of simple security measures such as locking up confidential documents, it also puts the spotlight on thorough background searches of employees of all levels, surveillance experts said.
"A lot of times companies say 'This person is just a secretary and I don't need to do everything on them as far as screening,"' said Jason Morris, president of employee screening firm Background Information Services. "Your secretary may not have the keys to the safe but he or she may have access to your CEO's e-mails, which could have the formula for a Coke product in them."
Friday, July 07, 2006
Hackers on Planet Earth July 21-23 in NYC
Over 100 speakers will have presentations on a variety of topics including computer hacking, phone phreaking, legal issues, wiretapping, cryptography, urban exploring, lockpicking, and spying. In addition we will present the return of a favorite panel: social engineering -- or how to get sensitive information from people who really ought to know better. A live demonstration of how to do this is planned.Also, Phil Torrone of Make will be speaking there, too. LinkAdditional talks include how to decode New York City's MetroCard, hacker filmmaking techniques, and even a discussion of hacker cooking. A panel of famous hackers who have gone to prison is also scheduled as is a study of the European hacker scene. And, in a first, there will be a "broadcast" of the WBAI hacker radio show "Off The Hook" in "indecent mode," designed to demonstrate the absurdity of current FCC policies.
Friday Fun! How to Deal With Being in Prison
Important Tips:
"Don't get caught up in a jailhouse romance. The last thing you need is to be getting involved in a relationship."
"Do not become a 'punk' (girlfriend). While becoming a punk might give you some fleeting, temporary protection from other inmates, you will be a virtual slave to one."
Air Force budgets $450K to data-mine blogs
The Air Force Office of Scientific Research recently began funding a new research area that includes a study of blogs. Blog research may provide information analysts and warfighters with invaluable help in fighting the war on terrorism. Drs. Brian E. Ulicny and Mieczyslaw M. Kokar, Framingham, Mass., will receive approximately $450,000 in funding for the 3-year project entitled “Automated Ontologically-Based Link Analysis of International Web Logs for the Timely Discovery of Relevant and Credible Information.”
Wednesday, July 05, 2006
nUbuntu Security Distro
 Anything based on ubuntu is a winner... So thanks GP for this great find! nubuntu is a security distribution which is derived from the Ubuntu distribution, with added packages related to security testing and with unneeded packages, such as Gnome, Openoffice.org, and Evolution removed.
Anything based on ubuntu is a winner... So thanks GP for this great find! nubuntu is a security distribution which is derived from the Ubuntu distribution, with added packages related to security testing and with unneeded packages, such as Gnome, Openoffice.org, and Evolution removed.Download nUbuntu 6.06 here.
Top 10 Information Security Skills
1. Communicate - I think that this is the most important information security skill, without being able to communicate it is hard to move ahead anywhere. Even if you have the best ideas in the world, if you cannot communicate them, no one will ever know.
2. Application Penetration Skills - being able to despin and understand how applications work, what protocols they use to communicate, what information is input and output from those applications, and best of all, how to make those applications do things that the programmer did not intend the application to do. This is the next major battle front in information security, and being able to move effectively in this space is important for future job success
3. Network Penetration Skills - being able to understand and use network properties like ARP, ICMP and TCP/IP to map, understand, and find vulnerable nodes on the network is a core skill.
4. Knowing what is a viable attack and what is not - tools that we use often spit out false positives, IDS systems, IPS systems, even our network and application penetration test tools all spit out false positives. Knowing which attacks against what target are viable and then being able to prove that viability to the developers and users of the system is a core skill.
5. Knowing how data migrates around the network - how is data used, where is it used, and who uses it in normal day to day patterns allows the Information security person to know when data is being misused, or someone who should not have access is trying to get access to it.
6. Network engineering skills - just enough to know how each component works on the network, what its function is, what its strengths and weaknesses are, and how it can be exploited.
7. IDS/IPS interpretation of results - being able to work with the IDS/IPS that is on the network and knowing how to find out more information about the data presented is a core skill. There is no sense in spinning up the whole department for a false positive, know how that IDS/IPS works, and what its limitations are.
8. System Administration - know enough about system administration that if presented with a series of computers, you can safely secure them allowing the applications to run that need to be on the box.
9. Risk Management skills - being able to understand the concepts of risk management, and how they are applied in regards to the companies culture. Not all companies are the same when it comes to risk management; each company has their own tolerance to risk. Be able to work within the confines of the companies tolerance for risk
10. Be creative - of all the top 10 skills that I am looking for, the ability to be creative when doing work makes the employee much more flexible, and easier to go forth and do good things.
Tuesday, July 04, 2006
Month of Browser Bugs
Ove the last few months, I have taken an interest in web browser security flaws. This interest has resulted in my collaboration on a few fuzzing tools (Hamachi, CSS-Die, DOM-Hanoi), a blog post, and a SecurityFocus article. The vendors have been notified and the time has come to start publishing the results. I will publish one new vulnerability each day during the month of July as part of the Month of Browser Bugs project. This information is being published to create awareness about the types of bugs that plague modern browsers and to demonstrate the techniques I used to discover them. Enjoy!
Saturday, July 01, 2006
You’re killing Palestinians, we’re killing servers
Unprecedented number of Israeli websites hacked: Hundreds of websites were damaged by hackers in recent hours, following IDF activity in the Gaza Strip. The hackers are members of the Moroccan “Team Evil” group, responsible for most of the website damage in Israel in the past year. This is the largest, most concentrated attack on Israeli websites in recent years.
A Ynet investigation revealed that more than 750 Israeli websites, on a number of different domains, were hacked into and damaged in recent days. Prominent among them were the Soldier’s Treasury Bank, Bank Hapoalim (not the main page), Rambam Hospital, the Society for Culture and Housing, BMW Israel, Subaru Israel, Jump Fashion, non-profit organization “Yedid,” Kadima’s youth website, and the Globus Group ticket center. Many of these sites have not yet returned to normal.
Hackers left the message: You’re killing Palestinians, we’re killing servers.
Wednesday, June 28, 2006
Saturday, June 24, 2006
Job Security - Never Leave Your Desk
 Internet Urinal
Internet UrinalShopping, gaming, chat rooms, cyber-dating - the internet is such an addictive and time-consuming force, who's got time to go? With the Internet Urinal, you'll never have to leave your computer again. Imagine the freedom - destroy your opponents on network Quake without taking a break; drink as many cans of Jolt as you want and still be able to make that last important trade before the market closes. Each urinal is made with hard plastic and comes with a handy female adapter. Holds 32 oz. of liquid (same as a Big Gulp!).
Wednesday, June 21, 2006
Candy From Strangers
 Why do people pick up a USB stick and then insert it into their computer during a security audit as was written about here? Are USB sticks that cool? What else would you just pick up and insert?
Why do people pick up a USB stick and then insert it into their computer during a security audit as was written about here? Are USB sticks that cool? What else would you just pick up and insert?
Saturday, June 17, 2006
Chinese Mobile Execution Bus

China Makes Ultimate Punishment Mobile
The country that executed more than four times as many convicts as the rest of the world combined last year is slowly phasing out public executions by firing squad in favor of lethal injections. Unlike the United States and Singapore, the only two other countries where death is administered by injection, China metes out capital punishment from specially equipped “death vans” that shuttle from town to town.
Makers of the death vans say the vehicles and injections are a civilized alternative to the firing squad, ending the life of the condemned more quickly, clinically and safely. The switch from gunshots to injections is a sign that China “promotes human rights now,” says Kang Zhongwen, who designed the Jinguan Automobile death van in which “Devil” Zhang took his final ride.
SQL SA Password Tips
The sa account is created during the installation process and the sa account has full rights in the SQL Server environment. By default, the sa password is blank (NULL), unless you change the password when you run the MSDE Setup program. To conform with the best security practices, you must change the sa password to a strong password at the first opportunity.
Verify if the SA password is blank
1. On the computer that is hosting the instance of MSDE to which you are connecting, open a command prompt window.
2. At the command prompt, type the following command, and then press ENTER:
osql -U sa
This connects you to the local, default instance of MSDE by using the sa account. To connect to a named instance installed on your computer type:
osql -U sa -S servername\instancename
You are now at the following prompt:
Password:
3. Press ENTER again. This will pass a NULL (blank) password for sa.
If you are now at the following prompt, after you press ENTER, then you do not have a password for the sa account:
1>
We recommend that you create a non-NULL, strong password to conform with security practices.
However, if you receive the following error message, you have entered an incorrect password. This error message indicates that a password has been created for the sa account:
"Login Failed for user 'sa'."
The following error message indicates that the computer that is running SQL Server is set to Windows Authentication only:
Login failed for user 'sa'. Reason: Not associated with a trusted SQL Server connection.
You cannot verify your sa password while in Windows Authentication mode. However, you can create a sa password so that your sa account is secure in case your authentication mode is changed to Mixed Mode in the future.
If you receive the following error message, SQL Server may not be running or you may have provided an incorrect name for the named instance of SQL Server that is installed:
[Shared Memory]SQL Server does not exist or access denied.
[Shared Memory]ConnectionOpen (Connect()).
Change your SA password
1. On the computer that is hosting the instance of MSDE to which you are connecting, open the command prompt window.
2. Type the following command, and then press ENTER:
osql -U sa
At the Password: prompt, press ENTER if your password is blank or type the current password. This connects you to the local, default instance of MSDE by using the sa account. To connect by using Windows authentication, type this command:
use osql -E
Note If you are using SQL Server 2005 Express, avoid using the Osql utility, and plan to modify applications that currently use the Osql feature. Use the Sqlcmd utility instead.
3. Type the following commands, on separate lines, and then press ENTER:
sp_password @old = null, @new = 'complexpwd', @loginame ='sa'
go
Note Make sure that you replace "complexpwd" with the new strong password. A strong password includes alpha-numeric and special characters, and a combination of upper and lower case characters.
You will receive the following informational message, which indicates that your password was changed successfully:
Password changed.
Friday, June 16, 2006
Friday Fun - Personality Type: The Backstabber
The Backstabber is yet another special personality type. Special, because it is The Backstabber & Backstabber alone, who keeps us between a prosperous life & a life full of poverty, hatred & depression (even a murderous life, if we choose to take it that far). For the sake of my own sanity & hopefully your own, I’m creating a list of Backstabberly characteristics that we must all memorize and attempt to pin onto people we live, work & play amongst. No one must be left out! It is a question of life & death, my friends. For safety, use the ‘3 strikes & you’re a fucking Backstabber’ rule.
1. The typical Backstabber will always be lurking. Lurking to see what you do, when you do it & how you do it.
2. In the office, the Backstabber might just be the person who comes to your cube unsuspectingly.
3. The Backstabber will always be first person willing to help when you need assistance—not because he genuinely wants to help, but because he wants to learn how you work & possibly expose weaknesses in the process.
4. The Backstabber, whenever the opportunity arises, will use the CC (or God forbid, the BCC!!) function in Microsoft Outlook.
5. The Backstabber will never take any blame upon himself. Never.
6. The Backstabber is also either a Drama Fanner or Drama Queen (personality types already covered The Bastardly).
7. The Backstabber pretends to be naive of very obvious things for the sake of seeing how you react.
8. The Backstabber’s main goal is to expose you in front of as many people as possible. In meetings they tend to laugh a lot, possibly ask stupid questions. Don’t fall into this stupidity trap. Their main goal is to get you to open your mouth, so that you may set yourself up for a beating.
9. All backstabbers are naturally very selfish & spoiled people. They will do anything to get the most and be the best. This includes whoring themselves, shady bribing techniques, hiring brothas to make hits—pretty much whatever it takes (think of the Terminator.)
10. Always know your Backstabber, but don’t become one yourself. It’s like the War On Terrorism—it will go on forever (or at least until one man is left standing). Basically, ignoring the Backstabber is not an option b/c that’s when you’re most vulnerable!
Remember, the only way to get a Backstabber off your back is to move to a different city, challenge them to an old-school duel, & of course, secede.
Godspeed!
Wednesday, June 14, 2006
British contractors shooting "A "trophy" video"
"The U.S. military has concluded its investigation into a video that appeared to show private security contractors shooting at civilian vehicles on highways in Iraq and determined that no one involved will be charged with a crime, a military spokesman in Baghdad said. The investigation, which officials have not released publicly, began after the video was posted on an Internet site purportedly run by employees of Aegis Defense Services, a London-based firm with a $293 million U.S. government security contract."
Naked Suspect Stunned By Oklahoma Police
The Daily Oklahoman
MIDWEST CITY -- Police used a taser to subdue a naked man seen streaking down SE 29, Police Chief Brandon Clabes said.
Mark Alan Oliver, 47, was taken into custody Monday night by two police officers while in the Village Oaks mobile home park in the 9400 block of SE 29.
Clabes said the man crawled under one of the mobile homes and refused to come out. Even after officers Archie Huston and Joe Cruz pulled the man from underneath the home, he continued to struggle until one of the policemen used a taser gun to subdue him, Clabes said.
Oliver was booked into the city jail on complaints of public intoxication and indecent exposure.
Clabes said Oliver told officers he had taken off his clothes to urinate and had forgotten where he left them.
Friday, June 09, 2006
Friday Fun - Windows' hidden "features"
Try this under Windows:
Right-click on the Desktop
Create a new Shortcut
Point the location of the item to any executable... such as: c:\windows\system32\calc.exe
Name the shortcut, for example, www.microsoft.com
Start Internet Explorer (IE5 and IE6 work best)
Type "www.microsoft.com" into the address bar
Enjoy.
More info can be found from here.
Saturday, June 03, 2006
Shredding scissors -- five-scissor blades on one handle
 These Japanese shredding scissors provide a low-tech way to discard of docs at your home or office desk.
These Japanese shredding scissors provide a low-tech way to discard of docs at your home or office desk.
Friday, June 02, 2006
Friday Fun - What E&Y Does Best!
The Register can again exclusively confirm the loss of the Hotels.com customer information after having received a copy of a letter mailed out jointly by the web site and Ernst & Young. A Hotels.com spokesman also confirmed the data breach, saying Ernst & Young notified the company of the laptop loss on May 3. The laptop in question was stolen from an Ernst & Young worker's car in Texas and did have some basic data protection mechanisms such as, erm, the need for a password.
Wednesday, May 31, 2006
"Weapon of Mass Destruction" Targets Sex Shop In FL
 In Waldo, people have held prayer vigils and protests aimed at an adult bookstore along US 301, trying to keep the "Cafe Risque" from opening its doors on time.
In Waldo, people have held prayer vigils and protests aimed at an adult bookstore along US 301, trying to keep the "Cafe Risque" from opening its doors on time.Those efforts have all failed, so investigators say it looks like someone has turned to what they're calling a clear act of terrorism to keep the store's owner from opening up shop.
Tuesday, May 30, 2006
Spam Or Ham
Although there are some existing sets of sorted messages available (such as the SpamAssassin public corpus and the TREC 2005 Public Spam Corpus), they are either small or have been sorted by machine and may contain errors.
SpamOrHam.org has been created to solve that problem by harnessing people power. By manually classifying (clicking This is Spam or This is Ham) a small number of messages a large number of people can quickly sort thousands of messages.
You can help out by clicking through messages that are randomly displayed and saying whether you think the message is spam or ham. It's as simple as that.
Saturday, May 27, 2006
Linux for Human Beings
"Ubuntu" is an ancient African word, meaning "humanity to others". Ubuntu also means "I am what I am because of who we all are". The Ubuntu Linux distribution brings the spirit of Ubuntu to the software world.
Great stuff...
Friday, May 26, 2006
Fridays are for Fun! No prison stay for 5-foot-1 child molester
 A man found guilty of sexually assaulting a child has been given 10 years of probation by a judge who said the man was too small to survive prison.
A man found guilty of sexually assaulting a child has been given 10 years of probation by a judge who said the man was too small to survive prison.District Judge Kristine Cecava of Cheyenne County sentenced Richard W. Thompson, 50, Tuesday on two counts of sexually assaulting a minor.
“What you have done is absolutely inexcusable,” she said.
His crimes deserved a long sentence, Cecava said, but she expressed concern that the 5-foot-1 Thompson would be especially imperiled by prison dangers.
Reporting Vulnerabilities - Not for the Faint of Heart
Nothing bad happened to me, but it could have, for two reasons.
The first reason is that whenever you do something “unnecessary”, such as reporting a vulnerability, police wonder why, and how you found out. Police also wonders if you found one vulnerability, could you have found more and not reported them? Who did you disclose that information to? Did you get into the web site, and do anything there that you shouldn’t have? It’s normal for the police to think that way. They have to. Unfortunately, it makes it very uninteresting to report any problems.
The second reason that bad things could have happened to me is that I’m stubborn and believe that in a university setting, it should be acceptable for students who stumble across a problem to report vulnerabilities anonymously through an approved person (e.g., a staff member or faculty) and mechanism. Why anonymously? Because student vulnerability reporters are akin to whistleblowers.
Thursday, May 18, 2006
Top ten spam-generating countries by Spamhaus.org
The US is the leading spam origin country. China and Russia are next.
Wednesday, May 17, 2006
Management Problems
This is true in any business environment, but it is especially true in the security world. Often executive management will look at security and see something that can be “fixed” with a magic box, maybe a firewall, an encryption device, etc.
However, the only way to really fix security is to have management truly understand the right reasons for needing an effective security program vs only perusing security due to external pressures/mandates to do so. Then once they have grasped this basic tenant then and only then can they successfully transmit this message to the troops.
Security can be looked at as an art or even a religion, but with out a foundation built on integrity, reality and wisdom… It is nothing but a lot of smoke and mirrors.
Sunday, May 07, 2006
Fridays are for Fun - Cryptography Rap
The rapper MC Plus+ has written a song about cryptography, "Alice and Bob." It mentions DES, AES, Blowfish, RSA, SHA-1, and more...
Computer-Savvy Thieves Rip-Off Gas Stations
At least two St. Louis gas station owners or managers say somebody is breaking into gas pumps, reprogramming interior keypads and instructing the machines to dispense fuel at no charge.
Free gas is certainly not what the gas station owners had in mind.
Kevin Tippit is manager of the Phillips 66 at Lindell and Boyle in St. Louis. Tippit says his boss lost between $6,000 and $10,000 worth of gas Friday before a regular customer tipped-off an employee.
"They (the thieves) have a key to the pump and then after they open up the pump they go in and they reprogram the pump, so they can have free gas. And then everybody behind them sees what they're doing, and they continue," says Tippit.
Wednesday, May 03, 2006
X-ray Machines Fail to Detect Assault Weapon
 Narcotics officers found the Professional Ordnance Carbon-15 Type-97 pistol in the car of a drug suspect in Newark and noticed it was a cut above the usual weaponry employed by local drug dealers, Fontoura said.
Narcotics officers found the Professional Ordnance Carbon-15 Type-97 pistol in the car of a drug suspect in Newark and noticed it was a cut above the usual weaponry employed by local drug dealers, Fontoura said.Officers in his ballistics laboratory, who said they had never seen an assault weapon made with so much plastic, had it taken to Newark Liberty International Airport earlier today for a test-run through the security scanners — minus its 30-round clip.
The image on the X-ray appeared as a straight metal rod, with no outline of a stock or a trigger guard, something an inattentive security guard may view as no more threatening than a curling iron, the sheriff said.
How a Boarding Pass Can Get You More Than a Plane Ride
Friday, April 28, 2006
The Use by Banks of Non-SSL Login Forms
Fridays are for Fun - Judge creates own Da Vinci code
 Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.
Per a BBC report, The Times and The Register the judge who presided over the failed Da Vinci Code plagiarism case at London's High Court hid his own secret code in his written judgement.Seemingly random italicized letters were included in the 71-page judgment given by Mr Justice Peter Smith, which apparently spell out a message.
Mr Justice Smith said he would confirm the code if someone broke it.
"I can't discuss the judgment, but I don't see why a judgment should not be a matter of fun," he said.
You can check it out for yourself here.
Thursday, April 27, 2006
Security Myths and Passwords
Policies requiring regular password changes (e.g., monthly) are an example of exactly this form of infosec folk wisdom.
From a high-level perspective, let me observe that one problem with any widespread change policy is that it fails to take into account the various threats and other defenses that may be in place. Policies should always be based on a sound understanding of risks, vulnerabilities, and defenses. “Best practice” is intended as a default policy for those who don’t have the necessary data or training to do a reasonable risk assessment.
Tuesday, April 25, 2006
Tool Time - Cmos password recovery tools 4.8
Works with the following BIOSes
* ACER/IBM BIOS
* AMI BIOS
* AMI WinBIOS 2.5
* Award 4.5x/4.6x/6.0
* Compaq (1992)
* Compaq (New version)
* IBM (PS/2, Activa, Thinkpad)
* Packard Bell
* Phoenix 1.00.09.AC0 (1994), a486 1.03, 1.04, 1.10 A03, 4.05 rev 1.02.943, 4.06 rev 1.13.1107
* Phoenix 4 release 6 (User)
* Gateway Solo - Phoenix 4.0 release 6
* Toshiba
* Zenith AMI
With CmosPwd, you can also backup, restore and erase/kill cmos.
Cain & Abel v2.8.9 released
- Added hashes syncronization functions (Export/Import) to/from Cain for PocketPC via ActiveSync.
- Added VoIP sniffer support for the following codecs: G723.1, G726-16, G726-24, G726-32, G726-40, LPC-10.
- Added support for Winpcap v3.2.
Download here.
Monday, April 24, 2006
Home Security - Man dies when large hole opens in home
Full story here.It was like a scene from a horror film: A 27-year-old man plummeted into a gaping hole that suddenly opened beneath a house, trapping him beneath foundation rubble and killing him.
"It's unbelievable," Placer County Sheriff's Department spokeswoman Dena Erwin said. "From the front of the house, it's absolutely normal. Then, in the middle of the house, is this enormous hole."
The victim was awake and on the ground floor about 9:30 p.m. Friday when the concrete foundation near the kitchen gave way, sending him plunging into to the ground, Erwin said.
Saturday, April 22, 2006
Super-Glue: Best practice for countering key stroke loggers

Read all the details in this article.
The one thing not mention in the article is that it is reported that Sumitomo Bank's best practice for avoiding a repeat attack is that they now super-glue the keyboard connections into the backs of their PCs.
Tuesday, April 18, 2006
Image stealing by phishers
From F-Secure Blog...
Lazy phishers are often simply making a copy of the original bank site with some malicious modifications. As an example, take a look at this currently active phishing site targeting Chase Bank.
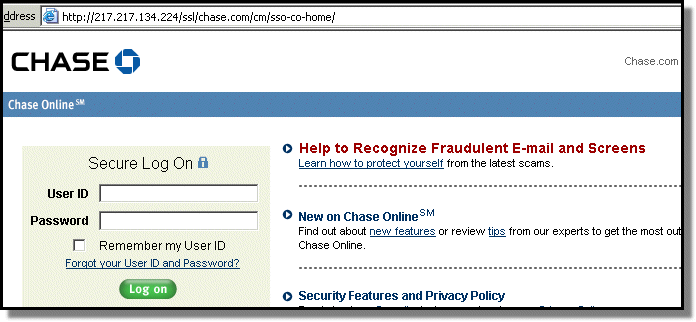
This phishing site is running on an infected home computer in Spain. Only the html is hosted there; all the images are actually loaded directly from a real chase.com server.
Now, activity like this could be detected by the website of the bank automatically. How about modifying the logic of the bank web server to do something along these lines:
If somebody
a) loads my images but
b) does not load the corresponding html file and
c) has http referrer -values outside of my domain
then, for this user, lets change this image:
to this image:

This could be activated only after the activity has happened from, say, 10 different IP addresses, to make it harder for the attackers to spot it until it's too late.
And, in most cases the REFERRER fields would directly point the bank staff to the real phishing site which they could now start closing down.
Eventually, attackers would move to host their own images, but for now they still typically don't.
Monday, April 17, 2006
Triple-DES Upgrade Adding Insecurities?
In a press release today, Redspin, an independent auditing firm based in Carpinteria, CA, suggests that the recent mandated upgrades of ATMs to support triple DES encryption of PINs has introduced new vulnerabilities into the ATM network environment - because of other changes that were typically made concurrently with the triple DES upgrades.
Sunday, April 16, 2006
Personal Security - So... You Think the Cold War is Over?
In a rare news conference, the designer of Russia's intercontinental ballistic missiles dismissed on Thursday a warning that Russia was falling behind the United States in the number of active nuclear warheads it has and said his Topol-M and Bulava missiles would serve as a sufficient deterrent until at least 2040.
"I assure you that the number of active warheads the strategic nuclear forces will have in 2015 and even in 2020 will be no less than 2,000," said Yury Solomonov, head and chief designer at the Moscow Institute of Thermal Technology, Russia's leading designer of intercontinental missiles.
Saturday, April 15, 2006
US Military Buys Back Stolen Flash Drives from Afghan Shopkeepers
Maps, charts, and intelligence reports on computer drives smuggled out of a US base and sold at a local bazaar describe how Taliban and Al Qaeda leaders have been using southwestern Pakistan as a key planning and training base for attacks in Afghanistan.
The documents, marked ''secret," appear to be raw intelligence reports based on conversations with Afghan informants, and official briefings given to high-level US military officers. Together, they outline how the US military came to focus its search for members of Taliban, Al Qaeda, and other terrorist groups on the border region with Pakistan and Pakistani territory.
American investigators have paid thousands of dollars to buy back the stolen drives, according to shopkeepers outside the major military base here, but many were still on sale yesterday.
Included on some drives were the Social Security numbers of hundreds of US soldiers, including four generals, and lists of troops who completed nuclear, chemical, and biological warfare training, the Associated Press reported.
Wednesday, April 12, 2006
Saturday, April 08, 2006
Forensic Analysis of the Windows Registry
Windows registry contains lots of information that are of potential evidential value or helpful in aiding forensic examiners on other aspects of forensic analysis. This paper discusses the basics of Windows XP registry and its structure, data hiding techniques in registry, and analysis on potential Windows XP registry entries that are of forensic values.
Friday, April 07, 2006
Fridays Are For Fun! - "Wow! That smarts."
A sheriff's deputy used a Taser to stop a 92-year-old man from allegedly beating his roommate with his aluminum cane at a Florida assisted living center.
Both men suffer from Alzheimer's disease, the center at Hudson, Fla., said. When struck by the Taser, Olin Holcombe's lone comment was, "Wow! That smarts."
A nurse reported hearing a "thud" shortly after midnight Thursday and she found Roland Casanova, 81, on the floor, defending himself from Holcombe's cane, the Tampa Tribune reported. The sheriff's deputy who answered the call said Holcombe swung the cane at him also before the officer drew his Taser.
"Wow! That smarts." ?! That's it? This guy's gets hit with a freekin' Taser, his pacemaker is probably vibrating faster than the toy-of-the-month on Sue Johanson's Sunday Night Sex Show, and all he says is "Wow! That smarts."
That guy is TUFF. I would've been laid out on the floor crying and wimpering, feeling something like a Mike Tyson cell mate after lights out.
A red-faced Australian nudist who tried to set fire to what he thought was a deadly funnel web spider's nest ended up with badly burnt buttocks, emergency officials said on Monday.
The 56-year-old man was at a nudist colony near Bowral, about 100 km (62 miles) southwest of Sydney, on Sunday when he spotted what he believed to be a funnel web spider hole.
Ambulance workers, including a helicopter crew, were called to the scene after the man poured petrol down the hole and then lit a match in an attempt to kill the offending arachnid.
"The exploding petrol fumes left the man with burns to 18 percent of his body, on the upper leg and buttocks," the NRMA Careflight helicopter rescue service said in a statement.
It said the man's lack of clothing probably contributed to the extent of his burns.
Tool Time - Online Pen-test tools
Wednesday, April 05, 2006
Internet Porn — Eye-Fi Commercial
The deputy press secretary for the U.S. Department of Homeland Security was charged with using a computer to seduce a child after authorities said he struck up sexual conversations with an undercover detective posing as a 14-year-old girl.
Sunday, April 02, 2006
Movie Plot Security Contest
Bruce Schneier is starting a contest:
"It is in this spirit I announce the (possibly First) Movie-Plot Threat Contest. Entrants are invited to submit the most unlikely, yet still plausible, terrorist attack scenarios they can come up with.
Your goal: cause terror. Make the American people notice. Inflict lasting damage on the U.S. economy. Change the political landscape, or the culture. The more grandiose the goal, the better.
Assume an attacker profile on the order of 9/11: 20 to 30 unskilled people, and about $500,000 with which to buy skills, equipment, etc."
You can post your movie plots on his blog here.
Saturday, April 01, 2006
Personal Security - Forget the Tinfoil Hat
ABC Suspends Producer Over Bush-Bashing E-Mail
ABC News suspended the executive producer of the weekend edition of "Good Morning America" yesterday over a pair of leaked e-mails in which he used inflammatory language to slam President Bush and Madeleine Albright.
In one of the e-mails, written during the first presidential debate in 2004 and leaked to the Drudge Report, Green wrote to a colleague on his BlackBerry: "Are you watching this? Bush makes me sick. If he uses the 'mixed messages' line one more time, I'm going to puke."
It is widely believed at ABC News that the e-mails were leaked by a former employee who has a vendetta against Green.
Friday, March 31, 2006
(IN)SECURE Magazine Issue1.6 (March 2006)
The covered topics are:
- Best practices in enterprise database protection
- Quantifying the cost of spyware to the enterprise
- Security for websites - breaking sessions to hack into a machine
- How to win friends and influence people with IT security certifications
- The size of security: the evolution and history of OSSTMM operational security metrics
- Interview with Kenny Paterson, Professor of Information Security at Royal Holloway, University of London
- PHP and SQL security today
- Apache security: Denial of Service attacks
- War-driving in Germany - CeBIT 2006
Tool Time - Ophcrack 2.2 Is Out
Thursday, March 30, 2006
The Code Room: Breaking Into Vegas
 In this episode of The Code Room watch the White Hats and Black Hats battle for the security of Las Vegas. Jessi Knapp and Microsoft Security Guru Joe Stagner narrate as the Hackers try to gain control of The Plaza's online money management system and our Security Team tries to stay one step ahead
In this episode of The Code Room watch the White Hats and Black Hats battle for the security of Las Vegas. Jessi Knapp and Microsoft Security Guru Joe Stagner narrate as the Hackers try to gain control of The Plaza's online money management system and our Security Team tries to stay one step ahead
Harvard and Berkley Study: Why Phishing Works
Tuesday, March 28, 2006
Firefox Bug Causes Breakup with Fiancé
 Sure blame the browser. The bug report makes for a fun read...
Sure blame the browser. The bug report makes for a fun read...How this particular privacy issue ended up in a relationship breakdown emerges from the bug report. The website designer that submitted the report writes that she had changed her mind when Firefox asked whether it should save the password for her website and dived into Password Manager to change her preference. What she found when she got there were the preferences of her fiancé: a list of dating and swinging websites that he had set to explicitly, and understandably, never save a password for…
News story here.
Hack Into Touch-Screen Voting Machine (undetected) and Win 10K!
Dr. Shamos, a professor of computer science at Carnegie Mellon University who has spent more than two decades testing electronic voting equipment, first made that offer several years ago. To this day, no one has tried to collect.
"Because they know they can't do it," he said last week.
Phishing With A New Twist
Not so for the attack on Capital City Bank, Wakulla Bank and Premier Bank in northern Florida. On March 14 hackers were able to break into the servers of ElectroNet, a Tallahassee, Fla. service provider which hosted the web sites for all three banks. The main business URL for the banks' were redirected to identical spoof sites on offshore servers, which asked customers to provide their login details.
The intrusion was detected about an hour after it started, ElectroNet CEO Allen Byington told the Tallahassee Democrat. Byington said that ElectroNet stores no confidential data on its computers and that the company was "working closely" with law enforcement agencies investigating the incident. The banks' sites were shut down for several days, and bank officials said the financial losses were "minimal," and that any customers who lost money were reimbursed by their respective banks.
Monday, March 27, 2006
Tool Time - EtherFlood
EtherFlood might be your answer. EtherFlood floods a switched network with Ethernet frames with random hardware addresses. The effect on some switches is that they start sending all traffic out on all ports so you can sniff all traffic on the network.
Details here.
You Are What You Post
Companies are increasingly googling the names of employees and potential employees to dig up information on them. Is what one finds on google an accurate representation of a person? What would your next boss find?
Saturday, March 25, 2006
Personal Security - Disney Film about Venereal Diseases
 Originally Released in 1973
Originally Released in 1973A general addressing his troops, which happen to be syphilis and gonorrhea germs. There are also characters representing ignorance and fear.
This is an educational short produced at the Walt Disney Studios.
Friday, March 24, 2006
In the News - SourceFire has been DPW'd. (Dubai Port World-ed)
From the Fridays Are For Fun Archives - You're In Control
 The You're In Control system uses an array of piezoelectric sensors mounted to the back of a urinal to detect the position of a stream of water, allowing a person to play a video game while peeing. A video monitor is mounted above the urinal, and position on the back of the urinal corresponds to position on the screen. We created a custom video game (our interpretation of the carnival game "whack-a-mole") in which the player attempted to hit hamsters as they flew out of one hole and into another hole in the ground. A successful hit would turn the hamster yellow, make it scream and spin out of control, and give the player ten points.
The You're In Control system uses an array of piezoelectric sensors mounted to the back of a urinal to detect the position of a stream of water, allowing a person to play a video game while peeing. A video monitor is mounted above the urinal, and position on the back of the urinal corresponds to position on the screen. We created a custom video game (our interpretation of the carnival game "whack-a-mole") in which the player attempted to hit hamsters as they flew out of one hole and into another hole in the ground. A successful hit would turn the hamster yellow, make it scream and spin out of control, and give the player ten points.IBM Demos ‘chip on a molecule’
 The first computer circuit to be built on a single molecule has been unveiled by researchers in the US.
The first computer circuit to be built on a single molecule has been unveiled by researchers in the US.It was assembled on a single carbon nanotube, a standard component of any nanotechnologist's toolkit.
The circuit is less than a fifth of the width of a human hair and can only be seen through an electron microscope.
The researchers, from IBM and two US universities in Florida and New York, told the journal Science that the work could lead to faster computer chips.
Wednesday, March 22, 2006
Firefox 2.0 Alpha Download
Download here.
Control your PC from an IRC room
You might find some other fun stuff on the related site - Script is here.
Monday, March 20, 2006
Cybersafety Campaign for Preschoolers Launched
Parents have more to worry about than their child grazing their knee in the playground -- they now should be concerned their toddlers are being kept "cybersafe" as well, an internet safety group said today.
A campaign to keep preschoolers safe when playing on the internet and with other modern technology is to be launched this week.
"In addition to young children inadvertently finding inappropriate material or being exposed to online predators and cyber bullies, they observe and copy the online behaviour of their parents and older siblings to an extent often not realised by their families," Ms Balfour said.
She cited the example of a New Zealand family that was surprised to receive a parcel of videos ordered online by their four-year-old.
"This experience just goes to show how well youngsters can copy behaviour."
"Young children may appear skilled in internet use, but they will not have yet developed the understanding and judgment to always keep themselves cybersafe," Ms Balfour said.






